How Dubai’s ISR V3.0 Is Shaping Smarter Security Standards in the region

Dubai’s commitment to strengthening cybersecurity governance has taken a definitive step forward with the release of the Information Security Regulation (ISR) Version 3.0. Developed and published by the Dubai Electronic Security Center (DESC), this regulation represents more than an administrative update. It serves as a foundational document for embedding cybersecurity into the operational core of every Dubai Government Entity (DGE), transforming abstract security principles into measurable, enforceable actions.
The ISR Version 3.0 does not merely echo international standards but adapts them to the specific functional and jurisdictional requirements of Dubai. This is a regulatory framework tailored for impact. Every control and sub-control, every expectation for ownership and review, reflects a calculated effort to ensure resilience across both technical and human elements of government operations. In the wake of expanding threat surfaces and a growing reliance on interconnected services, this regulation is a timely and essential guide to building long-term institutional security.
The Role of DESC: Strategic Custodian of Cyber Resilience
Before dissecting the regulation itself, it’s worth highlighting the orchestrator behind the ISR: the Dubai Electronic Security Center. The Dubai Electronic Security Center has long held a central role in defining, guiding, and enforcing cybersecurity within Dubai’s public sector. Its mandate spans policy development, capacity building, regulatory enforcement, and ecosystem leadership. In ISR Version 3.0, DESC’s position is even more entrenched, serving not just as the regulator but as a key enabler of consistent cybersecurity maturity across all DGEs.
DESC’s oversight includes reviewing exemption requests, certifying service providers, auditing compliance, and updating supporting frameworks that align with ISR implementation. Through ISR Version 3.0, DESC reinforces its stance that cybersecurity is not a matter of technological preference but one of governmental accountability. It sets the stage for security as a permanent, deliberate function embedded into every decision, policy, and digital transaction executed by public entities.
What Sets ISR Version 3.0 Apart
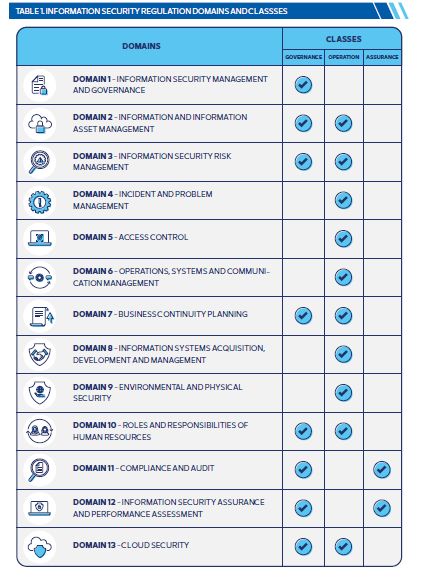
ISR Version 3.0 builds on the foundational 13-domain structure established in the previous version but enhances it through deeper specificity, expanded governance mandates, and a renewed focus on data handling and accountability. Each domain is framed by an overarching objective, supported by clearly defined main controls and sub-controls. These granular expectations guide government entities in not just securing their systems but also managing cyber risk as part of their day-to-day governance processes.
Unlike its predecessor, ISR V3 articulates a more rigorous approach to asset classification, access control, policy reviews, incident handling, and third-party relationship governance. It includes new language around modern security themes such as Zero Trust architecture, synthetic data protection, and risk-based policy alignment. The framework no longer allows flexibility as a passive strategy; instead, flexibility is now tied to documented risk assessments and the accountability of senior management.
For example, where Version 2 might have encouraged periodic policy reviews, Version 3 mandates minimum review cycles, involvement from executive leadership, and synchronization with DESC standards. Likewise, responsibilities of staff, from board members to temporary contractors, are now codified. All employees must undergo training and sign formal acknowledgements, and Information Security Champions must be appointed at the division level to ensure program fidelity across the organization.
Bridging From Version 2: From Compliance to Integration
Version 2 of the ISR provided Dubai Government Entities with the structural skeleton of a sound cybersecurity program. It introduced the concept of domains, defined high-level control areas, and emphasized the importance of aligning information security practices with business operations. However, many aspects of Version 2 were open-ended, allowing individual departments broad latitude in interpreting what “compliance” looked like.
Version 3 addresses this by introducing prescriptive measures. For example, in the area of information asset management, Version 2 required that assets be identified and classified. Version 3 now mandates that every entity maintain a living asset register, assign owners and custodians, and implement classification schemes that dictate access rights, retention policies, and disposal protocols.
Similarly, risk management in Version 2 focused on conducting assessments. In Version 3, the methodology must be documented, periodically updated, and the results approved by senior management or the Information Security Steering Committee. The shift here is not one of structure, but of depth and accountability.
Why ISR V3 Matters More Than Ever
Perhaps the most impactful evolution in ISR Version 3 is the transition from one-time compliance to continuous governance. There is now a clear expectation that every DGE must not only define controls but also measure their effectiveness through internal audits, DESC reviews, and performance assessments.
Controls cannot be implemented in isolation or left static. Version 3 enforces an ecosystem approach. Technical measures must be accompanied by awareness programs, contractual safeguards, executive sign-offs, and operational procedures. This convergence ensures that security decisions are validated by multiple disciplines within the organization.
Moreover, the regulation introduces required linkages to DESC-issued standards, including the expectation that only DESC-certified providers be used for security-related services. This adds another layer of integrity, helping standardize the quality and security of third-party engagements.
Practical Implications for Government Entities
For the average government department, ISR Version 3 translates into a comprehensive operational overhaul. Roles must be reassigned, documentation must be updated, and new monitoring practices must be embedded.
Internal audit teams must be qualified and independent. Confidentiality agreements must be legally enforceable and signed by all stakeholders. Third-party service providers must undergo risk assessments, and all contracts must include clauses enforcing data protection and system resilience requirements.
The responsibility doesn’t end with internal operations. ISR Version 3 expects DGEs to manage public-facing awareness as well. Information security training isn’t limited to new hires; it must be ongoing and adapted to emerging threats. Public portals must be used as education tools, and DESC encourages entities to promote cybersecurity hygiene within their broader ecosystems.
ISR V3.0: A Pillar Supporting Dubai’s Digital Strategy
In June 2023, Dubai unveiled the Dubai Digital Strategy, an ambitious framework to position Dubai as a global leader in digital transformation. Centered around seven strategic pillars, digital city, digital economy, data and statistics, digital talent, digital infrastructure, cybersecurity, and digital competitiveness, the strategy calls for the complete digitalization of government services, stronger data governance, and a robust digital economy fueled by innovation and security.
ISR Version 3.0 plays a pivotal role in enabling this vision, particularly within the pillars of digital infrastructure and cybersecurity. It provides the regulatory backbone required to secure digital services and ensure operational continuity across all government entities. By embedding cybersecurity governance into the DNA of public sector operations, ISR V3.0 helps create the trust and resilience necessary for a thriving digital ecosystem.
Where the strategy outlines goals like launching 50 seamless digital city experiences and increasing the digital wellbeing index, ISR V3.0 lays the security framework that ensures those digital initiatives are safe, resilient, and sustainable. Its mandates on asset classification, access controls, training, risk management, and vendor accountability directly support the Digital Strategy’s push toward agile, secure, and scalable services.
Moreover, ISR V3.0 complements Dubai’s intent to lead globally in digital competitiveness by introducing modern security paradigms such as Zero Trust architecture and risk-based decision-making. In doing so, it reinforces Dubai’s international credibility and positions the city as a model for safe digital transformation.
Ultimately, ISR Version 3.0 is more than a security policy, it’s an enabler of Dubai’s digital ambitions. As government entities align with its provisions, they contribute directly to a digitally empowered, secure, and globally competitive Dubai.
The Road Ahead: Cybersecurity as a Governance Imperative
Dubai’s ISR Version 3.0 doesn’t merely raise the bar. It redefines the field of play. Security is viewed as a structural component of government rather than a crisis response role. Information systems, public service trust, government operations continuity, and legal defensibility in the event of data incidents will all benefit from this strategy.
The function of DESC is still crucial. DESC makes sure that cybersecurity becomes as standard and unavoidable as budgeting or HR compliance by implementing stringent evaluation, flexible standards, and coherent policies. The focus is on maturity, and actions, not words, are the true test of adulthood.
Conclusion
ISR Version 3.0 represents a complete operational blueprint for cybersecurity institutionalization. Its effectiveness will depend not just on implementation but on the will of leadership across government entities to take accountability seriously.
In a world where disruption is often only one click away, Dubai has chosen not to wait. With ISR Version 3.0, it has drawn a definitive line: cybersecurity is governance, and governance must now begin with security.





 Governance and Policy Management
Governance and Policy Management