Unlocking Cyber Resilience with C2M2: How Complyan Helps You Navigate Cybersecurity Maturity

You’ve met the minimum requirements. Frameworks have been checked off, and regulators are content. However, you still don’t feel prepared for the challenges on the horizon.
Maturity goes beyond just compliance; it centers on resilience. This is where the Cybersecurity Capability Maturity Model (C2M2) becomes relevant, and how a tool like Complyan can help implement it effectively.
In this blog, we’ll not only analyze the C2M2 model, but also demonstrate how to transform it into a dynamic strategy that evolves with your team and enhances every aspect of improvement count.
What is C2M2?
The Cybersecurity Capability Maturity Model (C2M2) is a framework developed by the U.S. Department of Energy in collaboration with industry and government partners. Originally launched in 2012 and most recently updated as C2M2 version 2.1, the model is designed to assess and improve the cybersecurity capabilities of organizations, especially those operating in critical infrastructure sectors like energy, water, transportation, and manufacturing.
Rather than prescribing specific technologies or solutions, C2M2 focuses on capability domains, risk management, and organizational maturity. It is highly adaptable, allowing organizations to evaluate where they stand, where they need to improve, and how to build a sustainable cybersecurity strategy.
Why C2M2 Matters
- Industry-Neutral, Risk-Based Approach
C2M2 uses a risk-informed approach. It’s designed to be broadly applicable across industries, making it ideal for organizations that want to go beyond compliance.
2. Structured Maturity Progression
C2M2 breaks down cybersecurity into three maturity indicator levels (MILs) : MIL1, MIL2, and MIL3 , providing a practical way to measure progress.
3. Alignment with Existing Standards
C2M2 complements existing frameworks like NIST CSF, ISO 27001, and CIS Controls by acting as a maturity overlay.
4. Ideal for Operational Technology (OT)
C2M2 uniquely addresses both IT and OT, making it particularly relevant for critical infrastructure organizations.
The Structure of C2M2
The purpose of the C2M2 model was to offer descriptive, not prescriptive, instruction. Therefore, it provides 356 cybersecurity practices that are categorized into 10 areas according to important goals, instead of offering a list of restrictions or standards.
Below is a list of the ten domains along with an introduction to their context and practices:
C2M2 is organized into ten domains:
Asset, Change, and Configuration Management (ASSET): This domain evaluates an organization’s practices related to identifying, tracking, and managing its information assets, changes, and configurations. Effective management of assets helps in protecting critical data and systems.
Threat and Vulnerability Management (THREAT): This domain evaluates an organization’s plans, procedures, and technologies to detect, identify, analyze, manage, and respond to cybersecurity threats and vulnerabilities, commensurate with the risk to the organization’s infrastructure (such as critical, IT, and operational) and organizational objectives.
Risk Management (RISK): This domain assesses an organization’s ability to identify and manage cybersecurity risks effectively. It includes activities such as risk assessment, risk mitigation, and risk monitoring.
Identity and Access Management (ACCESS): This domain assesses how well an organization controls user access to its systems and data. It includes authentication, authorization, and access control measures to ensure that only authorized individuals can access sensitive information.
Situational Awareness (SITUATION): This domain focuses on an organization’s ability to monitor and detect cybersecurity threats and incidents in real-time. It involves security monitoring, threat intelligence, and incident response capabilities.
Event and Incident Response, Continuity of Operations (RESPONSE): This domain focuses on an organization’s ability to respond to cybersecurity incidents, maintain business continuity, and recover from disruptions.
Third-Party Risk Management (THIRD-PARTIES): This domain evaluates an organization’s controls for managing the cyber risks arising from suppliers and other third parties.
Workforce Management (WORKFORCE): This domain assesses an organization’s plans, procedures, technologies, and controls to create a culture of cybersecurity and to ensure the ongoing suitability and competence of personnel.
Cybersecurity Architecture (ARCHITECTURE): This domain focuses on the structure and behavior of an organization’s cybersecurity architecture, including controls, processes, technologies, and other elements.
Cybersecurity Program Management (PROGRAM): This domain evaluates an organization’s cybersecurity program that provides governance, strategic planning, and sponsorship for the organization’s cybersecurity activities in a manner that aligns cybersecurity objectives with both the organization’s strategic objectives and the risk to critical infrastructure.
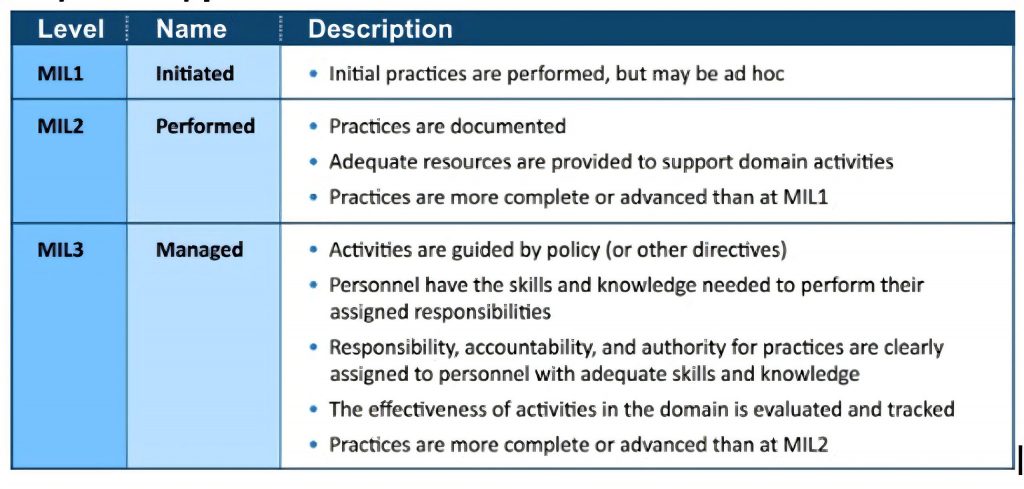
Maturity Indicator Levels (MILs)
To measure progression, the C2M2 uses a scale of maturity indicator levels, each representing maturity attributes described in the table below. Organizations that implement the cybersecurity practices within each MIL achieve that level.
The Cybersecurity Capability Maturity Model (C2M2) is a framework developed by the U.S. Department of Energy in collaboration with industry and government partners. Originally launched in 2012 and most recently updated as C2M2 version 2.1, the model is designed to assess and improve the cybersecurity capabilities of organizations, especially those operating in critical infrastructure sectors like energy, water, transportation, and manufacturing.
Rather than prescribing specific technologies or solutions, C2M2 focuses on capability domains, risk management, and organizational maturity. It is highly adaptable, allowing organizations to evaluate where they stand, where they need to improve, and how to build a sustainable cybersecurity strategy.
Why C2M2 Matters
- Industry-Neutral, Risk-Based Approach
C2M2 uses a risk-informed approach. It’s designed to be broadly applicable across industries, making it ideal for organizations that want to go beyond compliance.
2. Structured Maturity Progression
C2M2 breaks down cybersecurity into three maturity indicator levels (MILs) : MIL1, MIL2, and MIL3 , providing a practical way to measure progress.
3. Alignment with Existing Standards
C2M2 complements existing frameworks like NIST CSF, ISO 27001, and CIS Controls by acting as a maturity overlay.
4. Ideal for Operational Technology (OT)
C2M2 uniquely addresses both IT and OT, making it particularly relevant for critical infrastructure organizations.
The Structure of C2M2
The purpose of the C2M2 model was to offer descriptive, not prescriptive, instruction. Therefore, it provides 356 cybersecurity practices that are categorized into 10 areas according to important goals, instead of offering a list of restrictions or standards.
Below is a list of the ten domains along with an introduction to their context and practices:
C2M2 is organized into ten domains:
Asset, Change, and Configuration Management (ASSET): This domain evaluates an organization’s practices related to identifying, tracking, and managing its information assets, changes, and configurations. Effective management of assets helps in protecting critical data and systems.
Threat and Vulnerability Management (THREAT): This domain evaluates an organization’s plans, procedures, and technologies to detect, identify, analyze, manage, and respond to cybersecurity threats and vulnerabilities, commensurate with the risk to the organization’s infrastructure (such as critical, IT, and operational) and organizational objectives.
Risk Management (RISK): This domain assesses an organization’s ability to identify and manage cybersecurity risks effectively. It includes activities such as risk assessment, risk mitigation, and risk monitoring.
Identity and Access Management (ACCESS): This domain assesses how well an organization controls user access to its systems and data. It includes authentication, authorization, and access control measures to ensure that only authorized individuals can access sensitive information.
Situational Awareness (SITUATION): This domain focuses on an organization’s ability to monitor and detect cybersecurity threats and incidents in real-time. It involves security monitoring, threat intelligence, and incident response capabilities.
Event and Incident Response, Continuity of Operations (RESPONSE): This domain focuses on an organization’s ability to respond to cybersecurity incidents, maintain business continuity, and recover from disruptions.
Third-Party Risk Management (THIRD-PARTIES): This domain evaluates an organization’s controls for managing the cyber risks arising from suppliers and other third parties.
Workforce Management (WORKFORCE): This domain assesses an organization’s plans, procedures, technologies, and controls to create a culture of cybersecurity and to ensure the ongoing suitability and competence of personnel.
Cybersecurity Architecture (ARCHITECTURE): This domain focuses on the structure and behavior of an organization’s cybersecurity architecture, including controls, processes, technologies, and other elements.
Cybersecurity Program Management (PROGRAM): This domain evaluates an organization’s cybersecurity program that provides governance, strategic planning, and sponsorship for the organization’s cybersecurity activities in a manner that aligns cybersecurity objectives with both the organization’s strategic objectives and the risk to critical infrastructure.
Maturity Indicator Levels (MILs)
To measure progression, the C2M2 uses a scale of maturity indicator levels, each representing maturity attributes described in the table below. Organizations that implement the cybersecurity practices within each MIL achieve that level.
The Challenge: Applying C2M2 in the Real World
So what’s the catch?
While C2M2 is comprehensive and valuable, it can also be complex and time-consuming to implement.
Teams often struggle with:
- Mapping controls across domains and maturity levels
- Documenting progress in a consistent, auditable way
- Collaborating across departments (especially in large orgs)
- Turning assessment results into practical roadmaps
Without the right tools, the process can feel overwhelming.
Enter Complyan: Turning C2M2 Into an Actionable Strategy
Complyan isn’t just another governance or documentation tool, it’s a purpose-built platform that simplifies and streamlines the C2M2 journey.
Think of Complyan as your C2M2 command center. It guides your team through assessments, maps controls to the appropriate maturity indicators, and keeps everything organized in one place.
Here’s how Complyan helps bring the C2M2 framework to life:
1. Guided Assessments That Actually Make Sense
Complyan breaks down each domain and practice into plain language tasks and checklists, so even teams without deep compliance expertise can participate meaningfully.
No more interpreting dense framework documents or guessing what “Performed Level 2” really means.
2. Automated Evidence Collection and Tracking
As you document activities, Complyan helps automatically tag and organize evidence — whether it’s policies, logs, or audit trails.
This makes maturity tracking not only easier but audit-ready.
3. Visual Maturity Dashboards
One of the hardest parts of managing a cybersecurity program is showing progress.
Complyan solves that with real-time dashboards that let you visualize maturity across domains, spot gaps, and benchmark improvements over time.
It’s an easy way to answer executive-level questions with clarity and confidence.
4. Prioritized Roadmaps
C2M2 encourages you to improve, but doesn’t always say where to start.
Complyan helps generate prioritized action plans, based on your current maturity and the practices that will give you the biggest impact first.
That means faster progress, more meaningful improvements, and less guesswork.
5. Team Collaboration, Without the Chaos
Security maturity isn’t a one-person job. With Complyan, different team members and departments can contribute directly tracking responsibilities, assigning tasks, and maintaining accountability in one centralized platform.
C2M2 vs Other Cybersecurity Frameworks
FrameWork | Focus | Maturity Model Included | Industry Specific |
C2M2 | Capability maturity across ten domains | Yes | No |
NIST CSF | Risk-based controls and guidelines | No (but adaptable) | No |
ISO 27001 | Formal ISMS implementation | No | No |
CIS Controls | Technical controls and best practices | No | No |
C2M2 stands out for its maturity-based structure, making it ideal for measuring and improving implementation quality.
Conclusion
Cybersecurity maturity isn’t about how many tools you have, or how many boxes you’ve checked. It’s about whether your organization can withstand, respond to, and grow stronger after every threat that comes your way.
That’s what C2M2 is designed to measure not just where you are today, but how you improve over time.
Using Complyan to align with C2M2 practices can help organizations reduce costs in the long run. Gaps in cybersecurity maturity, especially those tied to non-compliance often leave systems vulnerable to breaches, which can be both financially damaging and reputationally costly.
By leveraging Complyan to stay on track with C2M2, teams can minimize those risks and redirect time, money, and effort toward initiatives that drive real value.
Ready to make cybersecurity maturity more manageable? Let’s talk.





 Governance and Policy Management
Governance and Policy Management