Compliance and GRC in 2026: What Organizations Should Expect and How Complyan Supports

Regulatory compliance has reached an inflection point. Organizations face pressure from multiple directions, including new AI regulations, stricter data protection laws, supply chain security mandates, and board-level demands for cyber risk visibility. The traditional annual audit approach no longer works when regulators expect real-time incident reporting and continuous control monitoring.
This shift creates both challenges and opportunities. Companies that treat compliance as a static checkbox exercise will struggle with mounting requirements and enforcement actions. Those that build integrated GRC programs with automation, continuous monitoring, and clear governance will turn compliance into a strategic advantage that enables faster growth and stronger customer trust.
The question isn’t whether to modernize compliance operations, but how to do it effectively without overwhelming security teams or creating administrative bottlenecks. Here’s what organizations should expect in 2026 and how Complyan helps address these challenges.
AI Governance Becomes Mandatory
Artificial intelligence has moved from innovation labs into production systems. Organizations use AI for customer service, fraud detection, hiring, and operational decisions. This adoption brings regulatory attention that organizations must address immediately.
The EU AI Act categorizes AI systems by risk level and imposes strict requirements on high-risk applications. If AI makes decisions about credit, employment, or access to essential services, documented governance processes are mandatory. This means tracking data sources, model training procedures, bias testing results, and decision audit trails.
The challenge isn’t just technical compliance. Organizations must explain how their AI systems work to regulators, customers, and affected individuals. This requires documentation that captures the entire AI lifecycle from initial design through ongoing monitoring.
Complyan AI approach focuses on practical implementation. The platform helps establish controls that satisfy regulatory requirements without creating bottlenecks in AI development. Automated evidence collection for model training, version histories, and compliance reports map directly to regulatory requirements.
Companies deploying AI need policies that specify acceptable use cases, required testing procedures, and approval workflows. Board members ask tough questions about AI risk, and organizations need answers backed by data rather than assurances. Executive reporting capabilities translate technical AI controls into business risk metrics that board members understand.
Security Automation Meets Compliance Requirements
Manual security processes fail at modern scale. Organizations receive thousands of security alerts daily. Human analysts cannot review every alert, investigate every anomaly, or respond to every threat in real time.
Security automation handles routine tasks, enriches threat data, and orchestrates response workflows. The compliance angle matters because automated systems make decisions that affect organizational risk. These systems need governance, documentation, and oversight.
Regulators expect timely breach notification. GDPR requires notification within 72 hours. The UAE’s PDPL has similar requirements. Manual processes struggle to meet these deadlines. Automated incident detection, classification, and notification workflows reduce response times from hours to minutes.
Complyan integrates compliance automation directly into security operations. The platform monitors security tool effectiveness, tracks control implementation, and maintains audit trails that prove compliance. Rather than periodic assessments that capture point-in-time status, organizations get continuous visibility into their compliance posture.
The automation extends to evidence collection. Security teams shouldn’t spend hours gathering screenshots, log files, and configuration data for auditors. Automated systems collect and organize evidence based on framework requirements. When auditors ask for proof of weekly vulnerability scanning, the evidence is ready.
Third-Party Risk Demands Continuous Monitoring
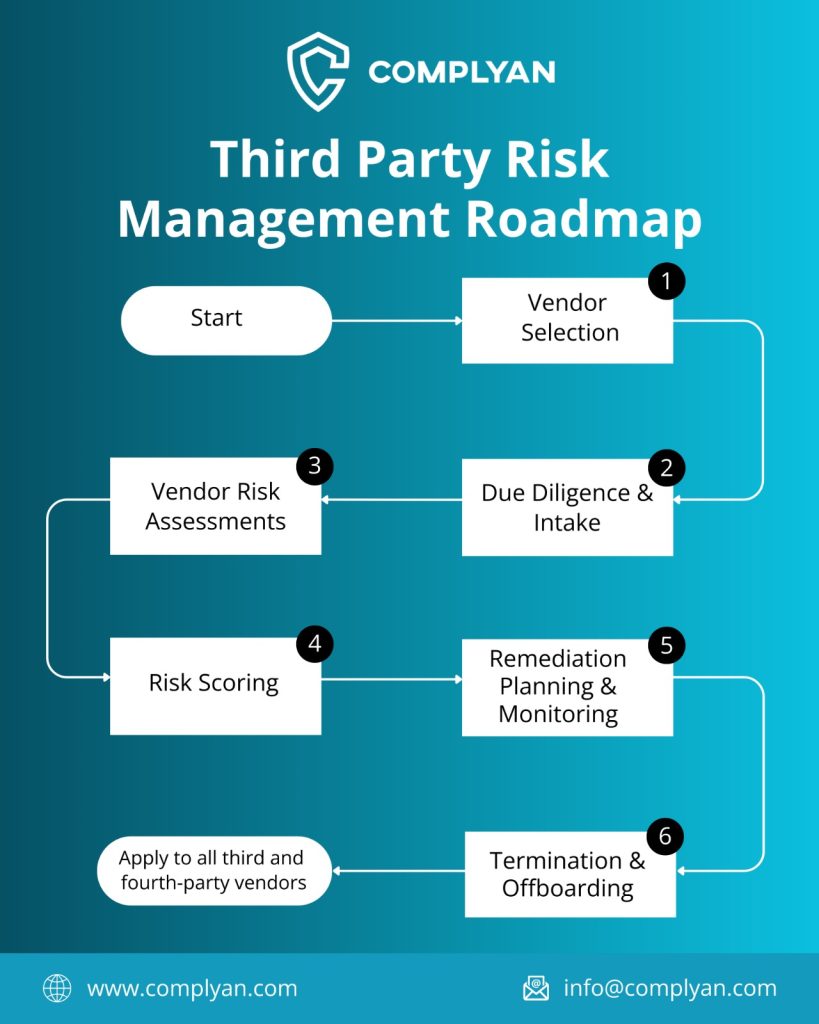
Supply chain compromises have shown that vendor security directly impacts organizational risk profiles. A vendor breach becomes a company breach when they process customer data or connect to internal systems.
The regulatory response has been swift and clear. The UAE’s PDPL holds organizations accountable for third-party data processing. DORA regulations require financial institutions to maintain detailed vendor risk programs. The ADGM’s cyber risk framework mandates ongoing vendor oversight with documented controls.
Traditional vendor assessments, annual questionnaires and occasional audits—don’t work anymore. Too many incidents occur where vendors passed assessments months before suffering major breaches. Organizations need continuous monitoring that tracks vendor security posture in real time.
Complyan’s approach to supply chain security combines automated vendor assessments with threat intelligence feeds. The platform monitors vendor security ratings, tracks breach notifications, and alerts organizations when vendor risk profiles change. This gives security teams early warning before vendor issues become organizational crises.
The system integrates vendor risk data into broader risk management workflows. When procurement considers a new vendor, risk data informs the decision. When contracts come up for renewal, current security posture matters. When vendors report incidents, the platform triggers notification and response procedures automatically.
Organizations need contractual protections that establish security requirements, audit rights, and incident notification obligations. Complyan helps clients develop vendor security requirements that map to their compliance frameworks and business needs. The platform then monitors vendor compliance with these contractual commitments.
Framework Updates Organizations Cannot Ignore
Compliance frameworks don’t stand still. Organizations must track updates to applicable standards and regulations, then implement necessary changes. Here’s what requires attention in 2026.
ADGM Cyber Risk Management Framework: The Abu Dhabi Global Market’s framework establishes comprehensive requirements for financial services firms operating in the free zone. Board-level oversight of cyber risks is mandatory. Incident reporting must occur within 72 hours. Resilience testing must happen regularly with documented results.
Complyan helps ADGM-regulated firms map their security programs to framework requirements. The platform maintains evidence that demonstrates compliance and tracks remediation timelines for identified gaps. When regulators request documentation, the required evidence is already organized and ready.
PDPL Implementation: The UAE’s Personal Data Protection Law continues to mature. Enforcement actions clarify regulatory expectations and demonstrate consequences for non-compliance. Organizations must implement technical measures that protect personal data, establish clear data processing agreements with vendors, and maintain documentation that proves compliance.
The law’s extraterritorial reach means companies outside the UAE must comply when processing UAE residents’ data. International organizations can implement PDPL controls and integrate them with existing privacy programs under GDPR or other regulations.
NIST Cybersecurity Framework 2.0: The updated framework elevates governance to a core function alongside identify, protect, detect, respond, and recover. This reflects reality—security requires executive commitment and organizational coordination beyond technical controls.
Complyan maps controls to the NIST framework and tracks implementation status across all six functions. Organizations can demonstrate framework alignment during assessments and identify gaps that require attention.
ISO 27001:2022: The latest ISO standard revision emphasizes cloud security, supply chain risk, and threat intelligence. Organizations with existing certifications must transition to the updated standard. This requires gap assessments against new controls and documentation updates.
ISO 27001:2022 control mapping is built directly into the Complyan platform. Organizations can assess their current state against the new standard, identify gaps, and track remediation progress. When certification audits occur, evidence collection is automated based on auditor requirements.
Risk Posture Requires Real-Time Visibility
Annual risk assessments capture a moment in time that’s outdated before the report is finished. Organizations need continuous risk posture management that reflects current threats, control effectiveness, and business context.
Complyan aggregates data from security tools, compliance assessments, and business systems to provide unified risk views. This integration shows how specific vulnerabilities or compliance gaps translate into business risk. Security teams can prioritize remediation based on actual risk rather than theoretical severity scores.
The SEC’s cybersecurity disclosure rules require public companies to report material incidents and describe their risk management processes. Organizations need capabilities that support these requirements through continuous monitoring and clear reporting mechanisms. The platform provides the documentation and audit trails that satisfy regulatory scrutiny.
Board members expect regular briefings that translate technical details into business implications. They want to know what risks the organization faces, how those risks compare to risk appetite, and what actions management is taking. Executive dashboards provide this visibility with trend analysis that shows risk posture over time.
Building Programs That Scale
Organizations should take specific actions to strengthen their compliance programs for 2026 and beyond.
Conduct comprehensive gap analysis: Review current programs against applicable regulations and frameworks. Assessment capabilities identify where requirements have changed or where existing controls fall short. The analysis produces prioritized remediation plans with timelines and ownership.
Establish cross-functional governance: Compliance requires coordination between security, legal, privacy, and business teams. Break down silos through shared workflows and unified risk data. Collaboration tools enable these teams to work together effectively.
Implement continuous monitoring: Deploy tools that provide real-time visibility into compliance status. Automate evidence collection, track control effectiveness, and alert teams when compliance status changes. This reduces manual effort while improving accuracy.
Build systematic vendor risk programs: Develop structured approaches to assessing, monitoring, and managing third-party risks. Integrate vendor risk management with procurement processes so risk considerations inform vendor selection from the start.
Invest in meaningful security automation: Identify repetitive tasks that automation can handle reliably. Start with alert triage, vulnerability scanning, and compliance reporting. Connect security automation with compliance requirements so automated actions maintain audit trails and satisfy regulatory expectations.
Document AI governance comprehensively: For organizations using AI, establish policies that address data usage, model training, bias testing, and decision review. Build documentation that supports regulatory inquiries and demonstrates responsible AI practices.
Enable executive visibility: Create reporting mechanisms that communicate risk and compliance status to boards and senior leadership in business terms. Translate technical metrics into business risk language that drives informed decisions.
How Complyan Supports Modern Compliance Programs
The platform addresses the reality that compliance in 2026 requires integration, automation, and continuous visibility. Organizations cannot succeed with disconnected tools and manual processes.
Several key capabilities address the challenges outlined above:
Framework mapping: Current mappings to major compliance frameworks including ISO 27001, NIST CSF, SOC 2, GDPR, PDPL, and ADGM requirements allow organizations to assess compliance status across multiple frameworks simultaneously and identify overlapping controls that satisfy multiple requirements.
Automated evidence collection: Security and IT tools generate evidence continuously. The system collects and organizes this evidence based on framework requirements so it’s ready when auditors need it.
Continuous monitoring: Rather than point-in-time assessments, the platform provides ongoing visibility into compliance status. When controls drift out of compliance, alerts notify responsible teams immediately.
Vendor risk management: Comprehensive third-party risk management includes initial assessments, continuous monitoring, and incident tracking. Organizations maintain complete visibility into vendor risk profiles.
Executive reporting: Technical compliance data translates into business risk metrics. Board members and executives get clear visibility into compliance status, risk trends, and remediation progress.
Workflow automation: Compliance activities follow defined workflows with approvals, documentation, and audit trails. This ensures consistent execution and maintains evidence for regulatory scrutiny.
Conclusion
The compliance requirements facing organizations in 2026 are more complex and demanding than previous years. Organizations that build integrated compliance programs with strong governance, continuous monitoring, and cross-functional collaboration will manage these requirements effectively.
Those relying on annual audits, manual processes, and disconnected tools will struggle to keep pace with regulatory expectations. The gap between leaders and laggards will grow as regulations mature and enforcement intensifies.
Organizations spend less time collecting evidence and more time improving their security posture when compliance operations are modernized. Demonstrating compliance becomes straightforward with real-time visibility into programs.





 Governance and Policy Management
Governance and Policy Management