Dubai Electronic Security Center (DESC) Compliance: What Organizations Operating in Dubai Must Get Right

Dubai’s ambition to operate as a digitally resilient city is enforced through a formal regulatory structure rather than high-level policy statements. At the center of this structure sits Dubai Electronic Security Center (DESC), the authority responsible for setting and enforcing cybersecurity requirements across government entities and regulated private organizations in the Emirate.
DESC compliance is not optional for entities that fall within its scope. It directly influences licensing outcomes, government procurement eligibility, audit posture, and operational continuity. Organizations that approach DESC as a documentation exercise tend to discover gaps late in the process, often during external reviews or regulatory engagement. Those that treat it as a structured security program tend to move faster, with fewer surprises.
Why DESC Exists and What It Enforces
DESC was established to create consistency in the implementation of cybersecurity across Dubai’s digital ecosystem. Rather than relying on voluntary standards, DESC issues enforceable requirements that apply to government departments, semi-government bodies, critical infrastructure operators, and private sector entities that process sensitive government or citizen data.
The most widely referenced DESC mandate is the Information Security Regulation (ISR), which defines baseline security controls, governance expectations, and risk management requirements. ISR Version 3 further tightened expectations around asset classification, third-party risk, incident response readiness, and security governance accountability.
DESC also extends into operational technology and industrial control environments, particularly where OT systems intersect with public services or critical infrastructure. This makes DESC relevant beyond traditional IT teams and places it firmly on the executive leadership agenda.
Understanding the ISR Framework
The Information Security Regulation serves as the cornerstone of DESC’s cybersecurity requirements. This comprehensive framework breaks down into 13 distinct domains that address every aspect of information security across Dubai Government entities and organizations operating within the emirate.
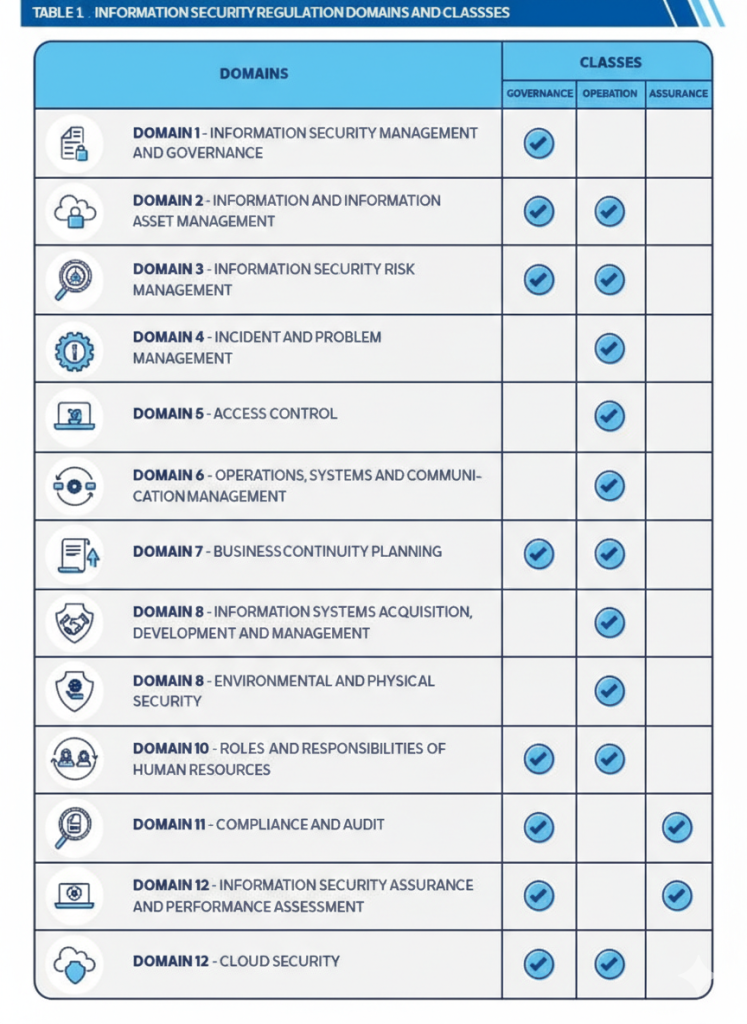
The framework organizes security requirements into three main categories: Governance, Operation, and Assurance.
Governance Domains establish the foundation for security management:
- Information Security Management and Governance
- Information and Information Assets Management
- Information Security Risk Management
Operational Domains focus on day-to-day security activities:
- Incident and Problem Management
- Access Control
- Operation, Systems and Communication Management
- Business Continuity Planning
- Information Systems Acquisition, Development and Management
Assurance Domains ensure accountability and continuous improvement:
- Compliance Management
- Human Resources Security
- Physical and Environmental Security
- Third Party Management
- Monitoring, Audit and Review
Each domain contains specific controls and sub-controls that organizations must implement based on their risk profile and the criticality of information they handle.
The Transition from ISR Version 2.0 to Version 3.0
DESC announced the release of ISR Version 3.0 in 2023, building upon the achievements and lessons learned from Version 2.0. This transition represents a significant evolution in Dubai’s approach to cybersecurity governance.
Achievements of ISR Version 2.0
Before examining the changes in Version 3.0, understanding Version 2.0’s impact provides important context. ISR V2 achieved several notable outcomes:
Government entities increasingly adopted cloud services hosted within the UAE, while international cloud service providers established presence in the country to serve the Dubai market. The number of service providers seeking DESC’s Cloud Service Provider Security Standard certifications grew substantially, indicating market responsiveness to regulatory requirements.
Organizations strategically restructured their security functions, making information security independent departments reporting directly to top management. This structural change improved control effectiveness and compliance monitoring capabilities. Usage of DESC services by government entities increased, accompanied by heightened awareness of information security practices among government staff.
Zero Trust and Modern Security Concepts
Version 3.0 incorporates contemporary security frameworks including Zero Trust architecture. Rather than assuming trust based on network location, organizations must verify every access request and continuously validate security posture. This approach aligns with global security trends recognizing that perimeter-based defenses no longer provide adequate protection.
The regulation also addresses synthetic data protection, reflecting growing use of artificial intelligence and machine learning in government services. Organizations developing or deploying AI systems must implement appropriate safeguards for training data, model security, and output validation.
Who Needs to Comply with DESC?
DESC compliance applies to a broad range of entities operating in Dubai:
Government Entities: All Dubai government departments and semi-government organizations must implement ISR requirements to protect citizen data and critical services.
Critical Infrastructure Operators: Organizations managing essential services including telecommunications, energy, transportation, healthcare, and financial services face stringent compliance obligations.
Private Sector Organizations: Businesses processing customer data, managing digital platforms, or utilizing cloud services must align their security practices with DESC standards.
Cloud Service Providers: Companies offering cloud infrastructure, platform, or software services to Dubai-based clients must demonstrate compliance with ISR cloud security specifications.
The regulation applies not only to full-time employees but also to consultants, contractors, and visitors who engage with government entities through various means. This comprehensive scope ensures security measures cover the entire operational ecosystem.
Steps to Achieve DESC Compliance
Step 1: Gap Assessment
Begin with a comprehensive evaluation of current security posture against ISR requirements. This assessment identifies areas where controls are missing, inadequate, or require enhancement. Organizations should evaluate all 13 domains, documenting current practices and comparing them against Version 3.0 requirements.
Step 2: Prioritize Remediation
Address high-risk vulnerabilities first, focusing on areas that could have the most significant impact on operations or data protection. Consider regulatory deadlines, resource availability, and dependencies between controls when developing implementation roadmaps.
Step 3: Policy Development
Create or update security policies to align with DESC requirements. Policies should address all domains within the ISR framework, clearly defining roles, responsibilities, and procedures. Ensure executive leadership reviews and approves policies, demonstrating management commitment to security.
Step 4: Technical Implementation
Deploy required security controls including firewalls, intrusion detection systems, endpoint protection, security information and event management platforms, and backup solutions. Configure systems according to DESC specifications and industry best practices.
Step 5: Cloud Security Review
For organizations using cloud services, conduct thorough security assessments of cloud configurations, ensure proper encryption, implement identity and access management, and establish continuous monitoring. Verify that cloud service providers hold valid DESC certifications.
Step 6: Training Programs
Develop and deliver security awareness training to all employees, ensuring they understand their responsibilities and can identify potential threats. Appoint Information Security Champions as required by Version 3.0 to maintain security focus across organizational divisions.
Step 7: Documentation
Maintain comprehensive records of all policies, procedures, risk assessments, security controls, incident response activities, and compliance activities. Documentation serves as evidence during audits and supports continuous improvement efforts.
Step 8: Testing and Validation
Conduct vulnerability assessments and penetration testing to validate the effectiveness of implemented controls and identify any remaining gaps. Testing should cover all critical systems, applications, and network infrastructure.
Step 9: Formal Audit
Engage an authorized third-party assessor to conduct a formal compliance audit. Address any findings and obtain certification. Maintain open communication with auditors throughout the process to clarify requirements and resolve issues promptly.
Step 10: Continuous Improvement
DESC compliance requires ongoing effort. Maintain continuous monitoring, conduct annual reassessments, update controls as threats evolve, and refine processes based on lessons learned. Participate in DESC information-sharing initiatives to stay informed about emerging threats and regulatory updates.
How Complyan Supports DESC Compliance
Achieving and maintaining DESC compliance can be complex, especially for organizations without dedicated cybersecurity teams. Complyan provides comprehensive support throughout the entire compliance journey, helping organizations meet ISR Version 3.0 requirements efficiently.
Complyan’s platform automates compliance tracking across all 13 ISR domains, ensuring nothing falls through the cracks during implementation. The solution helps organizations conduct gap assessments, prioritize remediation activities, manage policies and procedures, and prepare for audits with confidence.
With deep expertise in Dubai’s regulatory environment and the transition from ISR V2 to V3, Complyan guides organizations through the specific enhancements introduced in Version 3.0. From establishing Information Security Champion roles to implementing cyber-resilience frameworks, Complyan ensures compliance efforts address all new requirements.
Organizations can leverage Complyan’s knowledge base to understand how ISR requirements apply to their specific circumstances, access templates for required documentation, and track progress toward certification. The platform’s automated reporting capabilities provide real-time visibility into compliance status, helping leadership make informed decisions about security investments.
Common Challenges and Solutions
Resource Constraints
Many organizations struggle with limited cybersecurity expertise and budget constraints. Leveraging compliance management platforms and engaging external consultants can bridge these gaps efficiently. Complyan’s platform reduces the manual effort required for compliance management, allowing internal teams to focus on high-value security activities.
Technical Complexity
Legacy systems and complex IT environments make implementation challenging. A phased approach that prioritizes critical systems while planning long-term modernization helps manage this complexity. Organizations should develop transition roadmaps that balance immediate compliance needs with strategic infrastructure improvements.
Cultural Resistance
Employees may view security requirements as obstacles to productivity. Comprehensive training that emphasizes personal responsibility and organizational benefits helps overcome resistance. Information Security Champions can serve as advocates within their divisions, demonstrating how security practices protect both the organization and individuals.
Keeping Pace with Change
The cybersecurity field evolves rapidly, and DESC requirements are updated periodically. Establishing continuous monitoring and improvement processes ensures organizations remain compliant as standards evolve. Participating in DESC working groups and industry forums provides early visibility into upcoming regulatory changes.
Integrating DESC with Broader UAE Compliance Obligations
DESC does not exist in isolation. Many organizations in Dubai must also comply with UAE Information Assurance requirements, sector regulators, and data protection laws. Treating each obligation separately increases operational complexity.
A unified GRC approach allows DESC controls to be reused where overlap exists, reducing duplication while maintaining regulatory integrity. This approach is particularly relevant for organizations already addressing UAE-wide assurance obligations. A related perspective on this alignment is covered in Complyan’s blog on UAE information assurance requirements:
https://complyan.com/blog/uae-information-assurance-regulation
Conclusion
DESC compliance, particularly with the enhanced requirements of ISR Version 3.0, represents a comprehensive framework for protecting digital assets and maintaining operational resilience in Dubai. The transition from Version 2.0 to 3.0 reflects Dubai’s maturation in cybersecurity governance, incorporating lessons learned from Version 2.0’s implementation while addressing contemporary threats and technologies.
Organizations operating in Dubai must view DESC compliance as an ongoing commitment rather than a one-time project. The framework’s 13 domains provide structure for building robust security programs that protect sensitive information, ensure business continuity, and maintain stakeholder trust.
Whether you’re just beginning your compliance journey with Version 3.0 or transitioning from Version 2.0, understanding the framework’s requirements and taking a structured approach to implementation ensures your organization remains secure, compliant, and competitive in Dubai’s dynamic business environment.





 Governance and Policy Management
Governance and Policy Management