ECC-1: 2018 Cybersecurity Framework: Achieving Compliance with Complyan
The Middle East has always been a trailblazer in adopting new technology, and countries like Saudi Arabia, Dubai, and Qatar are leading the charge. But with technology comes the growing threat of cyberattacks, and the Kingdom of Saudi Arabia is acutely aware of the risks it faces as it continues to push forward with its digital transformation.
The KSA National Cybersecurity Authority launched the Essential Cybersecurity Controls (ECC) to mitigate these risks. These controls are designed to mitigate the risk of internal and external cyberattacks and ensure that Saudi Arabia’s digital infrastructure remains secure.
In this blog, we’ll take a closer look at the ECC and how Complyan can help organizations achieve compliance with its specifications. We’ll explore the various domains, subdomains, and controls outlined in the ECC and explain how Complyan’s tools and resources can assist in developing an effective cybersecurity program. So, let’s dive in and discover how your organization can stay secure in the face of evolving cyber threats.
Understanding the Essential Cybersecurity Controls
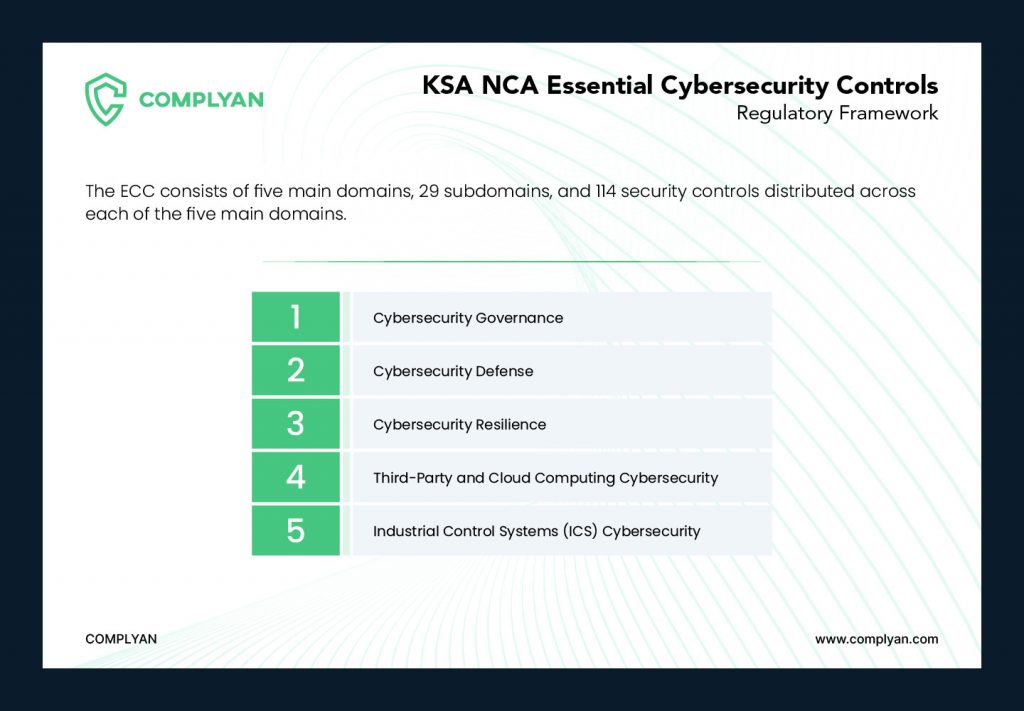
Cybersecurity Governance
The governance domain of the ECC focuses on establishing control over an organization’s cybersecurity operations. It provides best practices, and putting policies and procedures in place to safeguard the organization’s computer systems from cyber-attacks and recommendations for implementing a structured planning method, defining processes, and managing cybersecurity risks.
The 9 subdomains under governance include roles and responsibilities, risk management, information technology and project management, compliance with cybersecurity standards, laws, and regulations, periodical cybersecurity review and audit, and human resources. Each subdomain is designed with controls that address specific cybersecurity risks and compliance areas within an organization.
Cybersecurity Defense
The defense domain of ECC is concerned with planning, identifying, assessing, defending against, recovering from, and generally managing security risks before a disaster can occur or when a disaster occurs. It provides a range of security measures to help organizations be aware of security threats and have personnel and strategies in place to defend their systems.
- Asset management, the first subdomain of cybersecurity defense, entails making sure that the organization keeps an accurate and thorough inventory of its information and technology resources to support its cybersecurity program.
- Identity and Access Management (IAM) is another subdomain that involves setting up measures to ensure that only authorized users have secure, restricted access to the organization’s system while preventing unauthorized access.
- Other subdomains include but not limited to protection of information systems and information processing facilities, cryptography, email protection, network security management, and protection of mobile devices.
Cybersecurity Resilience
The resilience domain of ECC is focused on helping organizations build an overall resilient system in the face of cyberattacks. It provides guidelines on preparing for and mitigating cyber incidents to minimize their impact on systems and critical e-services.
This domain has only one subdomain: the Cybersecurity Resilience Aspects of Business Continuity Management. This subdomain provides controls to integrate resilience requirements into the organization’s business continuity management. By doing so, the organization can ensure that its critical business operations can continue even in the face of cyber incidents. The controls in this subdomain include strategies to mitigate the impact of cyber incidents on information processing facilities and systems and to enable quick recovery of e-services in case of disruption. By incorporating these controls into their business continuity management, organizations can improve their resilience and better protect themselves against cyber threats.
Third-Party and Cloud Computing Cybersecurity
The Third-Party and cloud computing cybersecurity domain guides the protection of an organization’s systems and data from cyber threats related to third-party integration and cloud computing resources.
The domain includes two subdomains: Third-party cybersecurity and cloud computing and hosting cybersecurity.
- Third-Party Cybersecurity, which provides controls to manage risks associated with third parties. These include software packages, contracts, outsourcing, and managed services. The controls aim to ensure that third-party integration complies with organizational policies, procedures, and relevant regulations and that all assets are protected from cybersecurity risks.
- The cloud computing and hosting cybersecurity subdomain provides controls to manage risks associated with cloud computing and hosting services. The controls ensure that information and technological resources hosted in the cloud or managed by third parties are protected from cyber threats. They also help ensure that efficient cyber risk remediation measures are in place.
Industrial Control Systems (ICS) Cybersecurity
Industrial Control Systems (ICS) is a computer-based system used in industries to monitor and control physical processes. The ICS Cybersecurity domain of ECC provides controls to ensure these systems’ proper and efficient cybersecurity management to protect them from cyber threats. The lone subdomain under this domain focuses on safeguarding the organization’s assets’ confidentiality, integrity, and availability against cyberattacks.
The controls provided in this subdomain are designed to protect ICS/OT systems against unauthorized access, destruction, spying, and fraud. These controls are developed per the organization’s cybersecurity strategy and applicable local and international laws and regulations. The subdomain covers risk assessment, access control, incident response, and personnel training. Additionally, it offers guidelines for mitigating potential threats and vulnerabilities as well as for ensuring the secure handling of information and technology resources in ICS/OT systems.
Applicability of ECC
How Can Complyan help Achieve Compliance with This Framework?

Complyan is a SaaS platform that offers a comprehensive suite of cybersecurity tools and services. It is designed to help organizations of all sizes meet the rigorous requirements of various cybersecurity frameworks, including the ECC-1: 2018. Complyan’s intuitive interface and user-friendly tools make it easy for organizations to manage risk, identify vulnerabilities, and stay up-to-date with the latest cybersecurity standards and regulations.
Complyan provides organizations with a variety of modules and features, including a risk management module that aids in the identification and assessment of potential threats, an incident management module that aids in the response to security incidents, and a compliance management module that streamlines compliance reporting and audits. The platform also provides a vendor management module that enables efficient management of third-party risks, a vulnerability management module that aids organizations in addressing potential security flaws, and a policy management module that enables the creation and enforcement of strong cybersecurity policies.
Using Complyan to streamline compliance with the ECC cybersecurity framework has numerous advantages, including:
- Customized compliance roadmap: Complyan can create a customized roadmap for an organization to ensure that it meets all the requirements of the ECC based on its specific needs, operations, and resources.
- Integrated compliance management system: Complyan provides an integrated compliance management system that enables organizations to manage their compliance with the ECC efficiently. The platform automates compliance tasks, tracks progress, and generates reports.
- Access to best practices: Complyan’s team of experts has extensive knowledge and experience in cybersecurity and can provide organizations with access to the best practices and latest trends in the industry.
- Risk assessment and management: Complyan can assist organizations in identifying and assessing their cybersecurity risks and develop strategies to manage and mitigate them.
- Ongoing compliance monitoring: Complyan can provide ongoing compliance monitoring and reporting to ensure that the organization remain compliant with the ECC over time.
- Continuous improvement: Complyan helps organizations to continuously improve their cybersecurity posture by identifying areas for improvement and recommending best practices.
- Expert guidance: Complyan’s team of cybersecurity experts can provide guidance and support throughout the compliance process, from initial assessment to implementation of controls and ongoing monitoring.





 Governance and Policy Management
Governance and Policy Management