How Complyan PTaaS Module Turns Complex Penetration Testing into a Streamlined Workflow

Organizations face a persistent challenge: identifying and remediating security vulnerabilities before attackers exploit them. Traditional penetration testing, while valuable, often involves lengthy engagement cycles, fragmented communication, and delayed reporting. The answer lies in modernizing the entire testing workflow, and that’s exactly what Complyan’s new PTaaS module accomplishes.
The Penetration Testing Bottleneck
A typical VAPT (Vulnerability Assessment and Penetration Testing) engagement follows a structured methodology. Security teams move through intelligence gathering, threat modeling, vulnerability mapping, exploitation, and post-exploitation phases before delivering findings. While this approach is thorough, it creates several operational friction points.
Consider the standard workflow: testers discover vulnerabilities, document them in isolated tools, compile findings manually, cross-reference with CVE databases, calculate CVSS scores separately, then assemble everything into a report. Each handoff introduces delays. Stakeholders wait days or weeks for visibility into their security posture. By the time findings reach decision-makers, the window for rapid remediation has often closed.
The challenge isn’t just speed, it’s coordination. Penetration testing involves multiple parties: security analysts conducting tests, project managers tracking progress, clients reviewing findings, and remediation teams addressing vulnerabilities. When these groups work in disconnected systems, critical information gets lost in translation.
What PTaaS Actually Solves
Penetration Testing as a Service addresses these coordination problems by centralizing the entire testing lifecycle into a single platform. Rather than bolting together separate tools for project management, vulnerability tracking, and reporting, PTaaS provides an integrated environment where all stakeholders operate from a shared source of truth.
This integration changes the economics of security testing. Organizations can run assessments more frequently because the overhead drops significantly. Teams can maintain continuous visibility into their security posture instead of relying on point-in-time snapshots that quickly become outdated.
The real value emerges in how PTaaS platforms handle the mechanics of vulnerability management. When a tester identifies a misconfigured Firebase database allowing unauthenticated reads, that finding needs proper classification, CVSS scoring, mapping to OWASP categories, and clear remediation guidance. Doing this manually for dozens of findings across multiple assets is tedious and error-prone. Automation makes it consistent and fast.
Inside Complyan’s PTaaS Module
Complyan’s PTaaS module reimagines how penetration testing projects flow from initiation to final reporting. The platform addresses specific pain points that security teams encounter during real-world engagements.
Centralized Dashboard and Project Intelligence
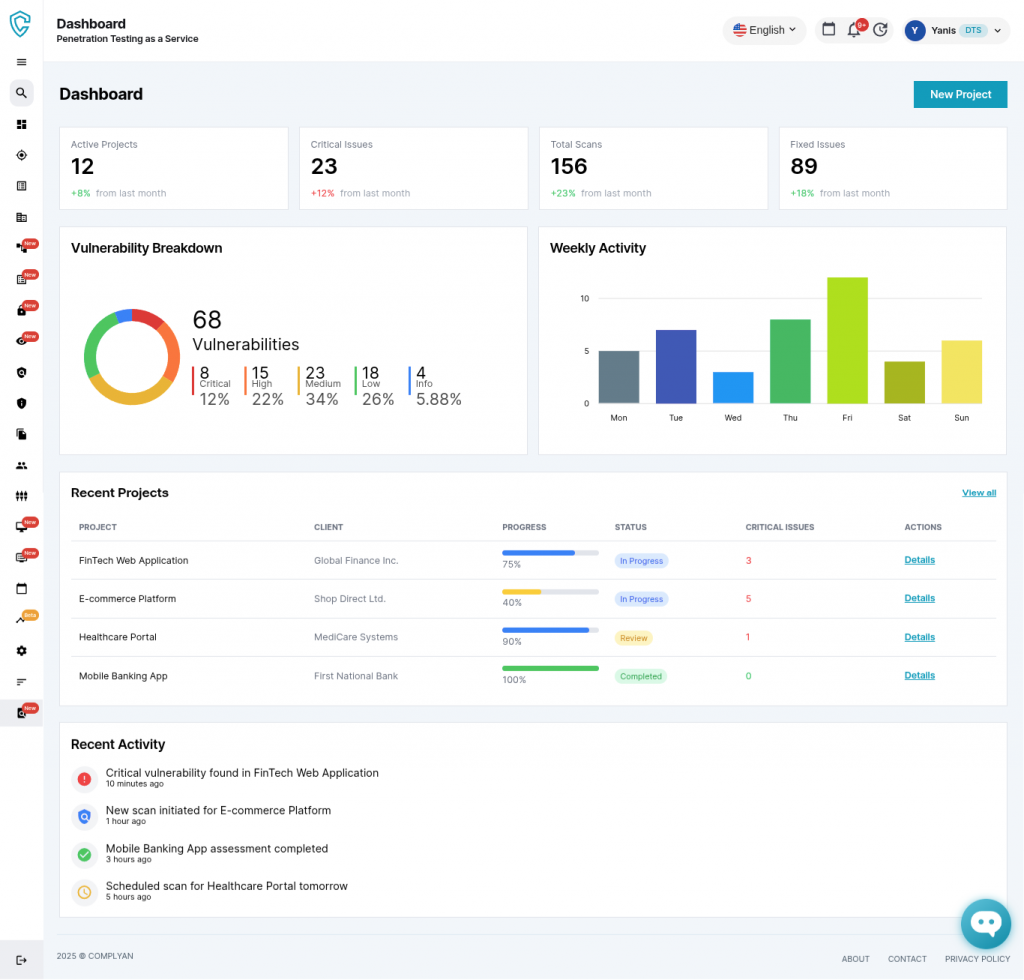
The unified dashboard provides complete visibility into testing operations. Security teams can track active projects, monitor critical issues, review scan totals, and measure remediation success from a single interface. Vulnerability breakdowns show severity distribution across the entire portfolio, while weekly activity charts reveal testing patterns and resource allocation.
Project listings display progress indicators, status updates, and outstanding issues for each engagement. Recent activity feeds provide real-time notifications about newly discovered vulnerabilities, completed scans, and ongoing assessments. This centralization eliminates the need for manual status reports and keeps all stakeholders aligned without constant meetings.
Comprehensive Vulnerability Visualization
The exploitation interface presents vulnerability data through multiple analytical views. Asset-based visualizations show how security issues distribute across the infrastructure. Exposure analysis breaks down internal versus external attack surfaces, helping teams understand where threats are most likely to originate. Severity metrics provide instant risk assessment through color-coded indicators.
The findings table organizes all discovered vulnerabilities with filtering and search capabilities. Each entry includes classification details, affected systems, current remediation status, and quick-access controls for editing or reviewing. This organized presentation enables security teams to quickly assess risk concentration and prioritize remediation efforts across complex testing engagements.
Integrated Security Testing Tools
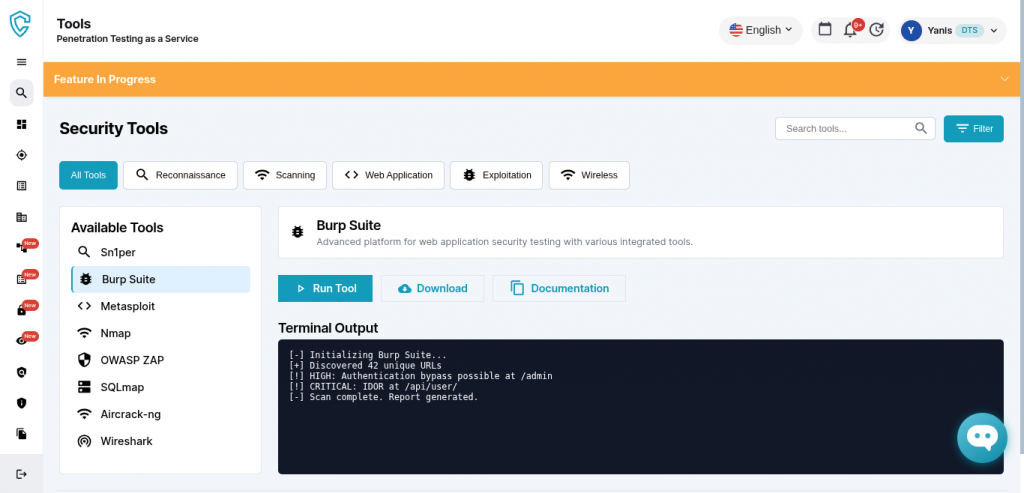
The platform includes a complete security tools suite directly accessible within the testing environment. Tools are organized by function: reconnaissance, web application testing, exploitation frameworks, network scanning, wireless assessment, and specialized security applications. Each tool can be launched directly from the interface with built-in documentation and download options.
Terminal output displays in real-time, showing scan progress and results as they happen. Tools like Burp Suite, Metasploit, Nmap, and OWASP ZAP run within the platform workspace, eliminating the context switching that slows traditional penetration tests. Testers execute reconnaissance, vulnerability scanning, and exploitation within a unified environment, maintaining workflow continuity throughout the assessment.
AI-Assisted Vulnerability Documentation
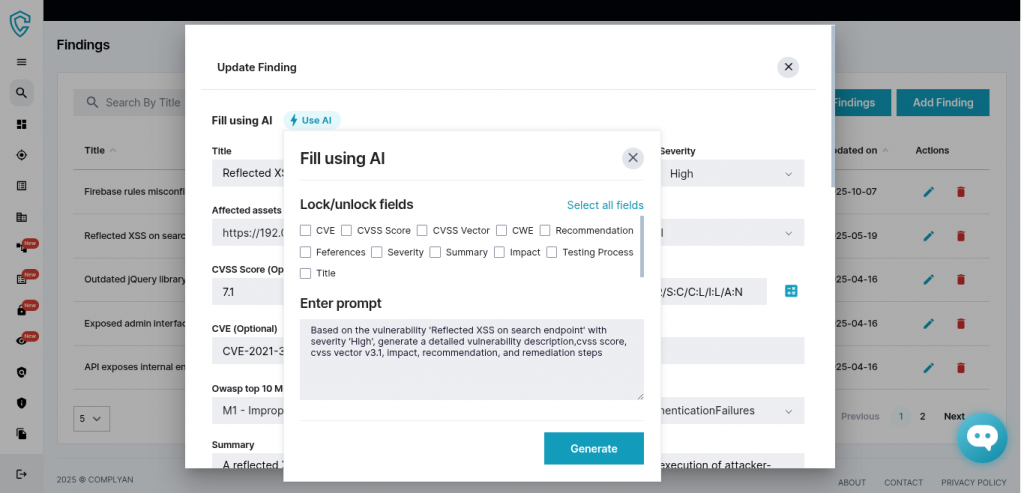
Manual vulnerability documentation consumes significant testing time. A tester discovers a security issue, then must write descriptions, document impact, suggest mitigations, calculate CVSS scores, and map to relevant frameworks. Repeating this for every finding is inefficient.
Complyan’s AI assistance handles this documentation burden. The system generates comprehensive descriptions, impact assessments, and remediation guidance based on vulnerability type and severity. The AI understands security context and provides appropriate recommendations for each finding category.
Testers can selectively apply AI assistance to specific documentation fields or generate complete vulnerability reports from simple prompts. This automation amplifies security expertise rather than replacing it. Testers focus on discovering and validating vulnerabilities while the platform handles standardized documentation, resulting in faster turnaround without sacrificing report quality.
CVSS Scoring and Standards Mapping
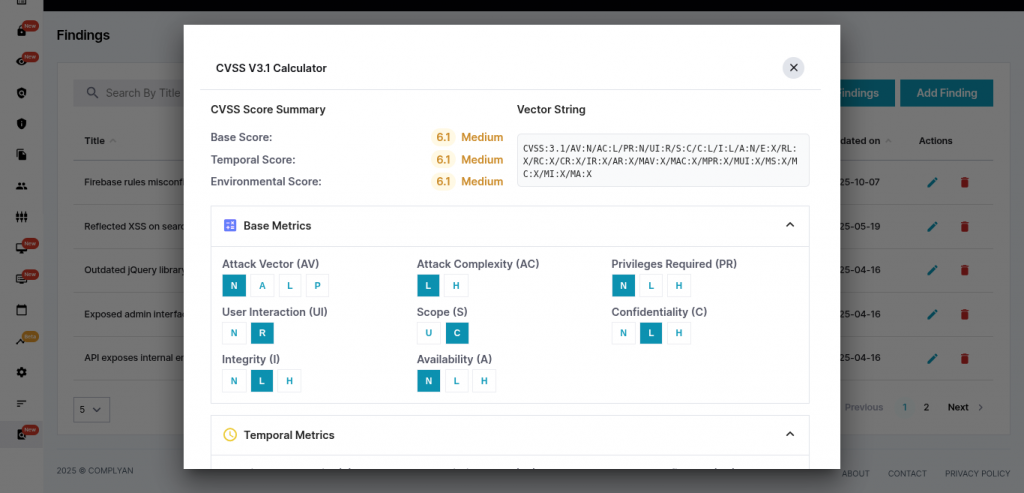
The CVSS v3.1 calculator walks testers through systematic vulnerability scoring. Base, temporal, and environmental scores are calculated based on selected metrics including attack vectors, complexity, required privileges, user interaction, and impact on confidentiality, integrity, and availability. The system generates complete vector strings for documentation and compliance purposes.
Beyond CVSS, the platform maps vulnerabilities to OWASP Top 10 categories, CWE classifications, and specific CVE identifiers. This automatic mapping is critical for organizations demonstrating compliance with security frameworks. When findings align with recognized standards without manual effort, compliance audits become straightforward and less resource-intensive.
Streamlined Reporting and Export
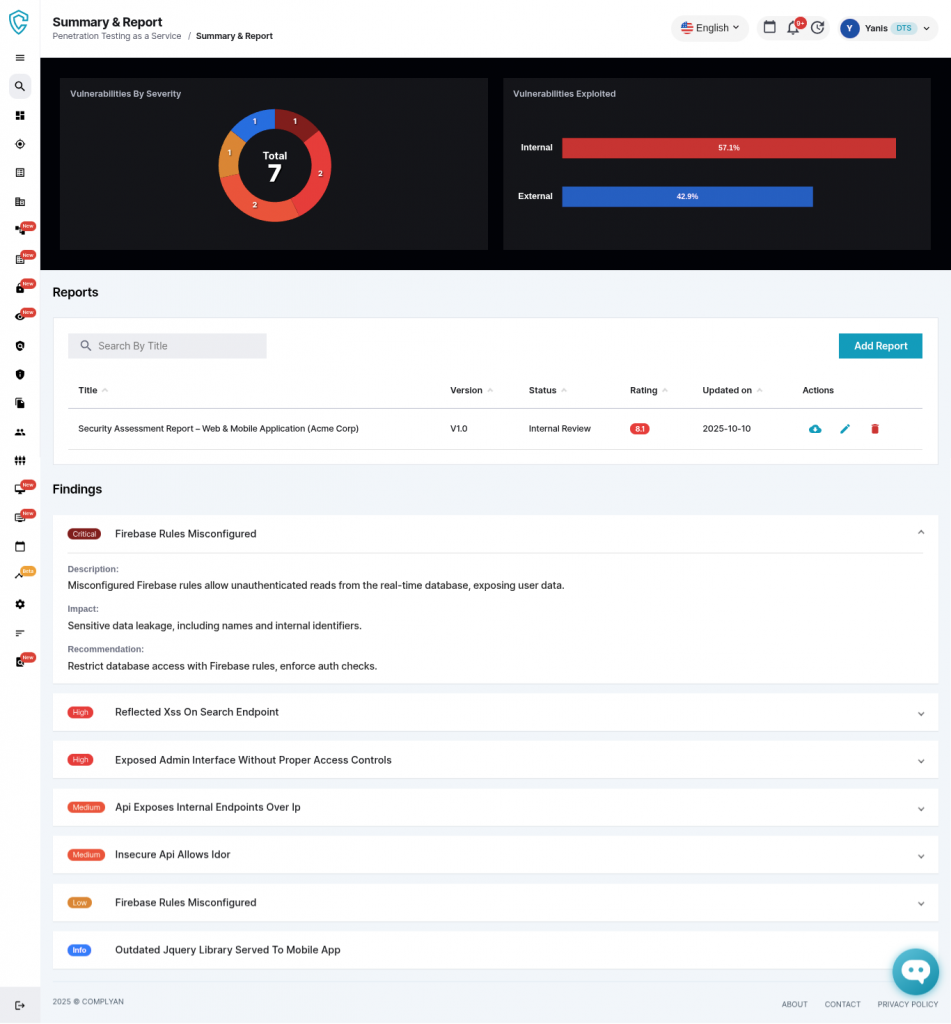
Once testing concludes, the reporting engine generates professional penetration testing reports automatically. The system assembles findings with all associated metadata, organizes content by severity, includes proof-of-concept evidence, and provides detailed remediation guidance in polished deliverables.
Export functionality enables seamless data exchange with external systems. Organizations can customize report templates to match branding requirements while maintaining technical rigor. The ability to regenerate reports instantly as findings update means clients can track remediation progress through successive versions rather than waiting for manual updates.
Practical Workflow Benefits
The integration of these components transforms how penetration testing engagements operate. Security teams create projects in the dashboard, define scope, assign members, and initiate scanning using integrated tools. As vulnerabilities surface, testers document findings using AI assistance for rapid, consistent descriptions.
Project managers monitor progress through real-time metrics. Clients access the collaboration workspace to review findings as they’re discovered rather than waiting weeks for final reports. Critical issues receive immediate attention because visibility is continuous, not delayed until report delivery.
When testing completes, comprehensive reports generate automatically with executive summaries, technical details, proof-of-concept evidence, CVSS scores, OWASP mappings, and prioritized remediation guidance. The platform handles the mechanical aspects of report compilation, freeing security professionals to focus on analysis and strategic recommendations.
Conclusion
Security testing is moving from periodic audits to continuous assessment. Organizations need the capability to test frequently, identify issues rapidly, and remediate effectively. PTaaS platforms like Complyan’s module make this shift practical by removing the operational friction that makes traditional testing slow and expensive.
The integration of unified dashboards, visual vulnerability analysis, embedded security tools, AI-assisted documentation, automated scoring, standards mapping, and instant reporting transforms what’s possible in security assessment. Teams can deliver more thorough testing in less time while maintaining the rigor that effective penetration testing requires.
For organizations serious about security, the question isn’t whether to adopt PTaaS—it’s how quickly they can integrate it into their security operations. The tools exist to make penetration testing smarter, faster, and more transparent.
Ready to experience the complete workflow from asset onboarding to automated reporting? Contact Complyan to see how the PTaaS module can transform your security testing program.





 Governance and Policy Management
Governance and Policy Management