What is Data Flow Mapping and Why Does Your Organization Need It?

When personal information moves through your organization, do you know exactly where it goes? Most companies collect customer data, process employee records, and share information with third parties daily. Yet many struggle to answer a simple question: what happens to that data after collection?
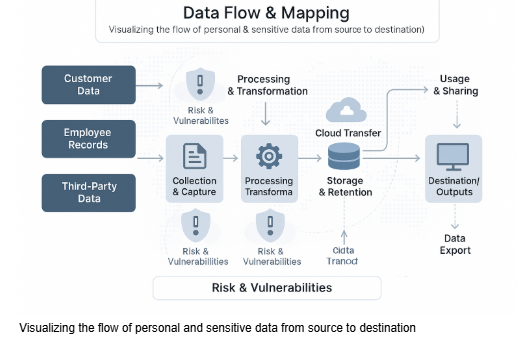
Data flow and mapping provides the answer. This practice tracks personal and sensitive information from its point of origin through every transformation, storage location, and destination. The result is a visual representation that reveals not just where data travels, but also where vulnerabilities hide.
Understanding Data Flow Mapping
At its core, data flow mapping creates diagrams that trace information movement through systems, networks, storage points, and external connections. These visualizations show the complete journey of data through your organization.
Consider a typical e-commerce transaction. A customer enters payment information, which moves to a payment processor, then to your database. Meanwhile, shipping details flow to logistics systems, and purchase history updates marketing platforms. Without mapping, this web of data transfers becomes impossible to secure properly.
The process identifies four critical elements:
External entities represent any outside source that interacts with your system—customer input forms, third-party APIs, email systems, or partner databases. These entities provide input or receive output data.
Processes include every action performed on data, whether manual or automated. Transformation, validation, encryption, and analysis all qualify as processes that must be documented.
Data stores encompass all repositories where information rests, from on-premises servers to cloud storage solutions. Each storage point represents a potential vulnerability that needs protection.
Data flows illustrate the actual movement between these components, showing how information travels from sources through processes to final destinations.
Why Data Flow Mapping Matters
Strengthening Security Posture
Mapping exposes weak points in your data protection strategy. When you visualize information flows, patterns emerge that reveal inadequate encryption, excessive access permissions, or unnecessary third-party transfers.
A financial services company discovered through mapping that customer social security numbers passed through seven different systems before reaching secure storage. Three of those transfers used unencrypted connections. Without the map, this vulnerability would have remained hidden until a breach occurred.
Data flow maps also accelerate incident response. When a security event happens, mapped systems help teams identify affected data and trace compromise paths within minutes rather than days.
Meeting Compliance Requirements
Regulations like GDPR, CCPA, and various industry standards demand detailed documentation of how organizations handle personal information. Data flow mapping provides exactly this documentation.
GDPR Article 30 specifically requires organizations to maintain records of processing activities. These records must show what data you collect, why you process it, who accesses it, and where it travels. A comprehensive data flow map satisfies these requirements while serving as an operational tool.
Different standards require organizations to demonstrate how sensitive data is transformed and protected. Visualizing data flows helps you comply with these frameworks while making it easier to understand applicable storage, processing, and transfer laws for various data sets.
Improving Operational Efficiency
Beyond security and compliance, data flow maps reveal operational bottlenecks. When you visualize information movement, you spot redundant processes, unnecessary copies, and inefficient routing.
One retail company discovered they were storing customer addresses in five separate databases. Mapping revealed that three of these copies served no business purpose and created unnecessary security risks. Eliminating redundant storage reduced costs while improving security
How to Create Your Data Flow Map
Creating effective maps requires systematic execution across six key steps.
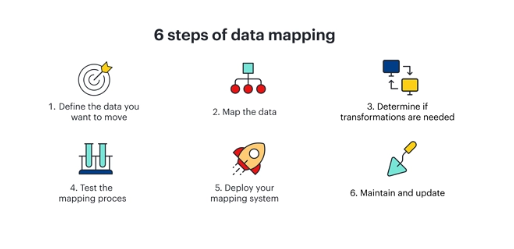
Step 1: Define Your Scope
Start by determining what data types your map will cover. Will you track all personal information or focus on specific categories like payment data or health records? Decide on the level of detail needed, high-level overviews work for executive presentations, while detailed subprocess maps help security teams.
Step 2: Identify Data Handlers
List every entity that touches your data. This includes internal departments, cloud services, on-premises systems, and third-party vendors. For each entity, document what data they access and why they need it.
Consider both obvious and hidden data handlers. That marketing analytics tool you installed last year? It probably receives customer behavior data. The backup system? It stores copies of everything. Overlooking any handler creates blind spots in your security posture.
Step 3: Catalog Personal Data
Locate every instance where personal information appears in your systems. This includes obvious items like names and email addresses, plus less obvious data like IP addresses, device identifiers, and behavioral patterns.
Pay special attention to sensitive categories. Financial records, health information, and children’s data face additional regulatory requirements. Tag these with appropriate classifications so your map highlights high-risk flows.
Step 4: Document the Journey
Trace how each data type moves through your organization. Start at collection points and follow information to its final destination or deletion. Note every transformation, does the data get encrypted, anonymized, or aggregated? Document transfer methods, are you using secure APIs or email attachments?
Automation tools can significantly streamline this discovery process, scanning systems to identify data locations and movement patterns. Automation reduces human error while accelerating map creation.
Step 5: Analyze Security Risks
With your map complete, evaluate each data flow for vulnerabilities. Look for unencrypted transfers, excessive access permissions, retention periods that exceed business needs, and unnecessary third-party sharing.
Ask critical questions: Does this process need access to raw data, or would anonymized information work? Could we encrypt this transfer? Do we need to store this data for seven years, or is that just habit?
Step 6: Maintain and Update
Data flows change constantly as you adopt new tools, modify processes, and adjust business practices. Schedule regular map reviews, quarterly for rapidly changing systems, annually for stable environments.
Common Challenges in Data Flow Mapping
Organizations frequently encounter three major obstacles when creating data flow maps.
Complexity overwhelms teams. Large companies with hundreds of systems and thousands of data flows struggle to create comprehensive maps. Start small, map one critical system or data type, then expand. Complete smaller maps provide more value than abandoned comprehensive projects.
Integration proves difficult. Different systems use incompatible formats, making it hard to trace data across platforms. Focus on documenting interfaces and transfer points rather than trying to map the internal workings of every system.
Tool limitations restrict visibility. Many mapping tools only work with specific platforms or require agents installed on every system. Choose solutions that integrate with your existing infrastructure and provide broad coverage across your technology stack.
Real-World Applications Across Industries
Data flow mapping delivers tangible value across different sectors and use cases.
E-commerce platforms map customer journeys from browsing through purchase to fulfillment. These maps reveal where customer data flows to marketing systems, payment processors, shipping partners, and analytics platforms. Clear visualization helps companies minimize data sharing while maintaining functionality.
Healthcare organizations map patient information flows to verify compliance with strict privacy regulations. These maps track data from electronic health records through billing systems to insurance companies, highlighting every point where patient privacy protections must be enforced.
Financial institutions map account data to meet banking regulations and prevent fraud. Visualizing money movement alongside information flows helps detect suspicious patterns while documenting compliance with financial privacy laws.
Supply chain operations use data flow mapping to track how vendor information, inventory data, and shipment details move between suppliers, warehouses, and distribution centers. This visibility helps identify where sensitive business information might be exposed.
Conclusion
Data flow mapping transforms how organizations understand and protect sensitive information. By visualizing exactly where data travels, you can identify vulnerabilities before breaches occur and demonstrate compliance to regulators with confidence.
Your data moves through your organization right now, following paths you may not fully understand. Mapping those flows brings the clarity needed to make informed security decisions, satisfy regulatory requirements, and optimize operational efficiency.
Ready to take control of your data flows? Contact us to learn how Complyan can help you build comprehensive data flow maps that protect your organization and your customers.





 Governance and Policy Management
Governance and Policy Management