Strengthening Cybersecurity in Saudi Arabia: The Role of the NCA ECC Framework

In recent years, the Kingdom of Saudi Arabia has rapidly advanced its approach to cybersecurity. At the center of this transformation is the National Cybersecurity Authority (NCA) and its Essential Cybersecurity Controls (ECC), a structured and comprehensive framework designed to bolster security across both public and private sectors. More than just a checklist, the ECC is a strategic mandate aimed at raising the Kingdom’s security posture and protecting national interests from cyber threats.
What is the NCA ECC?
The ECC, officially known as the “Essential Cybersecurity Controls,” was first introduced in 2018 by the NCA. It is a set of baseline cybersecurity requirements applicable to government bodies and organizations that own, operate, or host Critical National Infrastructures (CNIs). The 2023 update to the ECC builds upon lessons learned, global best practices, and localized needs to offer a more adaptable and practical implementation approach for organizations in Saudi Arabia.
The ECC goes beyond just regulatory measures; it embodies the nation’s commitment to safeguarding information assets, ensuring operational continuity, and maintaining sovereign security. Every clause of the ECC is designed to translate policy into action, helping organizations align with robust cybersecurity principles that integrate seamlessly into everyday operations.
While compliance with the ECC is mandatory for many entities, the framework serves a dual purpose: ensuring consistency across sectors and supporting a culture of security within every tier of the organization. In doing so, it lays the groundwork for a more unified and resilient cybersecurity ecosystem.
Key Changes in the ECC: From 2018 to 2024
Since the initial release of the Essential Cybersecurity Controls (ECC-1:2018), Saudi Arabia’s cybersecurity priorities and threat environment have evolved significantly. In response, the National Cybersecurity Authority introduced ECC-2:2024, a revised version that builds on the original framework while addressing new challenges and enhancing organizational maturity across sectors.
One of the most significant changes in ECC-2:2024 is the adoption of a tier-based compliance model. Under this model, organizations are classified into Essential, Advanced, or Minimal tiers based on their criticality and risk exposure. This shift enables more tailored and scalable implementations, helping organizations of different sizes and complexities meet relevant cybersecurity standards without employing a one-size-fits-all approach.
The updated framework also expands the number and depth of controls. Subdomains have been reorganized for better clarity, and the ECC now includes enhanced provisions for cloud computing, third-party risks, data protection, and emerging technologies. These changes align the framework more closely with globally recognized standards such as NIST CSF, ISO/IEC 27001:2022, and CSA CCM.
Another major enhancement is the improved compliance process. ECC-2:2024 introduces updated assessment tools and clearly defined evidence requirements, encouraging organizations to demonstrate not only control implementation but also security maturity and operational effectiveness over time.
With these upgrades, the ECC is no longer just a baseline checklist, it’s a strategic framework designed to elevate the Kingdom’s cyber resilience, support national trust, and future-proof critical systems in an increasingly digital world.
The Purpose Behind the ECC
The goal of the ECC is threefold:
- Create a unified security baseline across government and CNI sectors.
- Establish preventive and detective controls to address both known and emerging threats.
- Support national resilience by ensuring systems are not only secure but also recoverable.
These objectives are not abstract concepts, they are grounded in operational needs. The ECC emphasizes integration, but not isolation. Rather than treating cybersecurity as an afterthought, it calls for embedding security from the ground up, within processes, people, and technology.
It also encourages a shift in mindset. Cybersecurity is not simply about tools or policies; it is about cultivating awareness, accountability, and preparedness. The ECC helps organizations transition from reactive responses to proactive risk management, ensuring that security is part of the conversation at every level.
Who Needs to Comply?
The ECC is mandatory for:
- Government organizations and ministries
- Semi-government entities and authorities
- Private sector entities operating CNIs
These organizations must demonstrate compliance through audits and assessments led by accredited bodies. Non-compliance can result in reputational damage, regulatory penalties, and increased exposure to cyber risks.
However, the ECC’s influence extends beyond mandatory adoption. Even organizations not formally required to comply are increasingly aligning with the framework to build credibility, reduce risk, and position themselves as trustworthy partners in both local and global ecosystems.
Domains of the ECC Framework
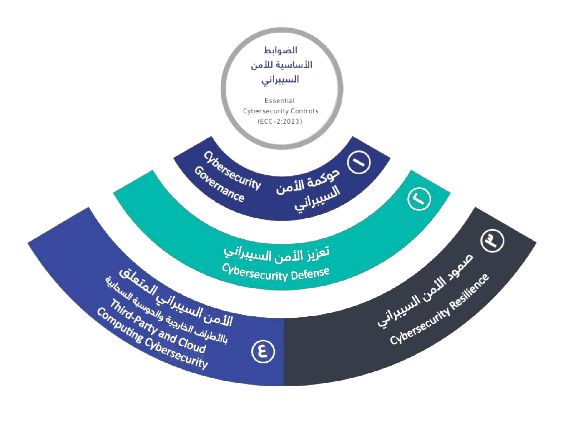
The ECC is organized into five main domains, each comprising multiple subdomains that cover the full spectrum of security priorities.
- Cybersecurity Governance
This domain lays the foundation for security leadership. It includes developing a cybersecurity strategy, assigning roles and responsibilities, creating security policies and procedures, and embedding security considerations into IT project management.
Governance is about setting direction and ensuring accountability. Without a strong governance structure, even the most sophisticated technologies or controls can fail due to a lack of oversight. This domain demands that cybersecurity be represented at the leadership table, not just within the IT department.
Additionally, it promotes a culture of ownership. When security is everyone’s responsibility, from executive leadership to front-line staff, the organization is better positioned to detect, prevent, and respond to threats.
- Cybersecurity Defense
This domain focuses on proactive and reactive defenses, encompassing asset management, network security, endpoint protection, data encryption, identity and access controls, and vulnerability management.
Defensive capabilities should be layered and coordinated. It’s not merely about firewalls or antivirus software. The ECC emphasizes the need for comprehensive visibility into digital assets, management of access points, and mechanisms for real-time threat detection and response.
Regular patching, secure configurations, and risk-based prioritization of vulnerabilities are critical. More importantly, defensive efforts must be continuously refined to reflect the ever-changing threat landscape.
- Cybersecurity Resilience
This component stresses preparedness for adverse events. Whether it’s an attack, system failure, or data loss, organizations must prove they can continue critical operations and recover promptly.
Resilience is not achieved overnight. It involves planning, testing, and learning. The ECC mandates the development of business continuity and disaster recovery plans, the implementation of regular backup protocols, and the establishment of incident response procedures.
These controls must be realistic, actionable, and regularly tested. A beautiful plan sitting in a binder is useless during a crisis. The ECC drives organizations to operationalize resilience through simulation, metrics, and post-incident reviews.
- Third-Party and Cloud Cybersecurity
The fourth domain recognizes that today’s organizations often depend on third-party vendors and cloud solutions. The ECC demands rigorous assessments of external partners’ security postures.
Controls here govern everything from procurement due diligence to SLAs (Service Level Agreements) that define responsibility during incidents. Cloud adoption is not discouraged, but it must be managed with discipline and transparency.
Organizations are accountable not only for their internal environment but also for the systems and data managed by their partners. This requires new levels of collaboration and communication across business units, legal teams, and procurement.
Implementation: From Paper to Practice
While the ECC outlines what must be done, it intentionally leaves room for organizations to choose how they implement these controls. The NCA provides a Guide to ECC Implementation to assist in interpreting requirements and integrating them into operations.
The guide offers illustrative examples, not rigid formulas highlighting deliverables, documentation templates, and evidence expectations. This flexibility acknowledges the diversity in organizational size, sector, and maturity.
However, implementation is not a one-time task. It requires:
- Periodic assessments
- Continuous monitoring
- Regular updates to documentation and infrastructure
Auditors can request evidence beyond what’s listed in the implementation guide, ensuring that security efforts are not just performative but practical. Organizations must treat ECC implementation as a dynamic, ongoing process rather than a compliance exercise with a finish line.
Challenges and Considerations
Complying with the ECC comes with several hurdles:
- Resource Allocation: Smaller entities may struggle to meet the same requirements as larger ones without tailored support.
- Cultural Shifts: Embedding cybersecurity into organizational culture takes time, particularly in sectors where it was previously overlooked.
- Evolving Threats: Although the ECC is periodically updated, organizations must remain vigilant against threats that may not yet be explicitly covered.
To address these challenges, organizations must promote internal collaboration among departments, invest in security training, and prioritize automation and scalability in their controls. The effort is significant, but the long-term benefits are worth it: a secure, compliant, and resilient organization.
The Strategic Impact
Beyond compliance, the ECC has strategic implications for both organizations and the Kingdom at large.
For organizations, it offers a roadmap to maturity. It supports operational reliability, builds stakeholder trust, and opens opportunities for local and international partnerships, especially with entities that prioritize compliance in their vendor ecosystem.
For the nation, the ECC contributes to sovereignty. In a world where cyber threats are increasingly used as geopolitical tools, a strong national cybersecurity posture is a form of defense as vital as any military resource.
Conclusion
The ECC is not just a regulatory framework, it is an enabler of long-term stability and operational integrity. For organizations in Saudi Arabia, it provides a structured approach to managing cyber risk, fostering resilience, and building trust across all levels.
Compliance should not be viewed as a burden, but as a strategic investment. Those who approach the ECC with commitment and foresight will not only meet requirements, they will position themselves as leaders in security excellence and future-ready operations.





 Governance and Policy Management
Governance and Policy Management