The Ultimate Guide to Third-Party Risk Management: Securing Vendors, Suppliers, and Data
As long as businesses rely on outside contractors to deliver essential services, there has never been greater demand for a robust third-party risk management program. Early detection and handling of any vulnerabilities resulting from third-party partnerships is necessary due to the dynamic nature of cybersecurity threats, operational interdependence, and regulatory duties.
Vendors, contractors, and even suppliers are integral parts of modern business operations. While these third-party relationships often provide cost-effective solutions with enhanced service delivery, they also bring various risks, some visible while others might be hidden. These risks can have far-reaching consequences, ranging from data breaches to regulatory fines. Managing these risks requires a systematic approach from assessing, to monitoring, to mitigating third-party vulnerabilities.
Defining Third-Party Risk Management (TPRM)
Third-party risk management is a comprehensive process used to identify and control these risks originating from external vendors. These risks may include cybersecurity threats, regulatory compliance failures, financial instability, operational disruptions, and reputational damage. As organizations integrate more external suppliers and partners into their business ecosystem, to ensure the integrity of data and critical operations, effective risk management is essential
A TPRM program serves as a structured approach to prevent, detect, and respond to risks posed by third parties. It involves not only initial assessments but also continuous monitoring of the vendor relationship to ensure that risks remain within acceptable thresholds.
Categories of Third-Party Risks
A thorough understanding of the different types of risks introduced by third-party vendors is crucial for an effective TPRM strategy. These risks can be categorized into several key areas, each with its own set of challenges and mitigation strategies.
1. Cybersecurity Risks
The growing reliance on third-party vendors increases an organization’s exposure to cybersecurity threats. Third parties often have access to sensitive data and internal networks, making them attractive targets for cybercriminals. A breach at a third-party vendor can lead to severe consequences, including data theft, malware infections, or system downtimes.
Cybersecurity risks introduced by third-party vendors include:
- Data Breaches: Unauthorized access to sensitive information stored or processed by the vendor.
- Malware and Ransomware: Attacks leveraging third-party vulnerabilities to spread malware across networks.
- Weak Authentication Practices: Vendors with poor identity and access management practices increase the risk of unauthorized access.
The 2024 MediSecure breach is a case in point, where attackers exploited a vulnerability in a third-party provider, compromising the medical and personal data of 12.9 million individuals.
2. Compliance and Regulatory Risks
Compliance and regulatory risks arise when third-party vendors fail to meet national or industry-specific legal obligations. In the context of the UAE and Saudi Arabia, organizations must now navigate several distinct cybersecurity and privacy mandates tailored to regional infrastructures and risk landscapes. Failure to comply with these can result in serious legal consequences and reputational damage.
UAE IA (Information Assurance): Mandatory security controls for UAE government and critical entities.
Dubai ISR (Information Security Regulation): Information security regulation for Dubai government bodies, covering 12 security domains.
UAE PDPL (Personal Data Protection Law): Federal law on personal data protection, consent, breach response, and cross-border rules.
NCA ECC (Essential Cybersecurity Controls): Baseline cybersecurity controls for Saudi government and critical infrastructure operators.
KSA PDPL (Personal Data Protection Law): Kingdom-wide data protection law enforced by SADIA, governs data use and processing.
Department of Energy (DOE) Cybersecurity Standards: Cybersecurity requirements for energy entities under UAE’s Department of Energy.
ADHICS (Abu Dhabi Healthcare Information and Cyber Security Standard): Cyber and privacy standards for healthcare providers in Abu Dhabi.
SACS-002 (Aramco Third-Party Cybersecurity Standard): Aramco’s vendor cybersecurity compliance framework for third-party suppliers.
These regional frameworks are not optional checklists. They are legally enforced, with real-world implications for procurement, vendor selection, and supply chain continuity.
Any organization partnering with government bodies or operating in regulated sectors within the UAE or Saudi Arabia must embed these requirements into their third-party risk assessment processes.
Organizations must ensure that their third-party vendors also comply with these regulations to avoid facing penalties for non-compliance. The absence of adequate data protection protocols, such as proper encryption or failure to report data breaches on time, could result in significant fines or lawsuits.
3. Operational Risks
Operational risks emerge when a third-party vendor’s failure disrupts the organization’s ability to function. These risks often arise when a vendor experiences downtime, service interruptions, or fails to meet contractual obligations. Examples include:
- Service Outages: Downtime caused by a vendor’s system failure or technical issues, impacting critical operations like e-commerce transactions or customer communications.
- Vendor Bankruptcy: Financial instability within a vendor organization could result in sudden termination of services or delayed project deliveries.
- Quality Failures: A third-party vendor that provides subpar services or products could negatively affect the organization’s performance or damage its reputation.
A prime example is the 2024 MOVEit breach, where attackers exploited an unpatched vulnerability in a widely used file transfer tool, leading to unauthorized access and the compromise of sensitive data across organizations in healthcare, finance, and government sectors.
4. Financial Risks
Financial risks from third-party vendors are often overlooked but can have significant consequences. If a vendor is financially unstable, it could affect the organization’s operations, leading to service disruptions or contract termination. The financial health of a vendor should be regularly assessed to ensure they are capable of meeting contractual obligations.
These risks include:
- Vendor Insolvency: Vendors facing financial difficulties might default on their commitments, causing delays or halting services altogether.
- Price Fluctuations: Vendors might adjust pricing unexpectedly, leading to unplanned cost increases.
- Unstable Business Models: Vendors with poorly diversified revenue streams are more vulnerable to market fluctuations, which could impact their ability to meet service agreements.
5. Reputational Risks
Third-party relationships can influence an organization’s reputation. If a vendor fails in its duties, such as compromising customer data or failing to meet contractual obligations, the organization’s brand can suffer as a result. Reputational risks include:
- Public Relations Damage: A third-party vendor’s failure may lead to negative press coverage and loss of customer trust.
- Brand Association: In the case of a data breach or compliance violation by a vendor, customers may perceive the organization itself as responsible, leading to long-term brand damage.
For example, In 2022, the Optus data breach, caused by a misconfigured API, exposed the personal data of nearly 10 million people and sparked public backlash, damaging the company’s reputation and trust.
Implementing a Strong Third-Party Risk Management Program
Effectively managing third-party risk requires a structured and systematic approach. This process includes several key steps:
1. Risk Identification
The first step is to identify and classify the third-party vendors that play a role in business operations. Vendors should be assessed based on their level of criticality to business functions, the sensitivity of the data they handle, and the access they have to internal systems.
Vendors should be categorized into:
- High-Risk Vendors: Those that handle critical data, such as customer information or intellectual property, or those providing services that are integral to business operations.
- Medium-Risk Vendors: Vendors providing non-critical but important services, like office supplies or non-sensitive data handling.
- Low-Risk Vendors: Vendors with minimal access to sensitive data or business systems.
2. Risk Assessment
After identifying the vendors, the next step is a comprehensive risk assessment. This assessment involves evaluating the likelihood and impact of potential risks that each vendor poses. This may include conducting technical audits, reviewing the vendor’s security controls, evaluating financial stability, and verifying compliance with regulatory standards.
This process should also involve the use of risk matrices or scoring systems to quantify and prioritize risks based on their potential impact and likelihood.
3. Vendor Due Diligence
Before engaging a new vendor, a thorough due diligence process is critical. This process includes:
- Cybersecurity Audits: This involves assessing the vendor’s security posture, including vulnerability assessments and penetration testing, and reviewing their incident response protocols.
- Regulatory Compliance Audits: Ensuring the vendor complies with relevant industry regulations and standards.
- Financial Health Checks: Analyzing financial reports, credit ratings, and any warning signs of financial distress.
4. Contractual Safeguards
Contracts with third-party vendors should contain clearly defined security requirements, compliance expectations, and penalties for non-compliance. Clauses related to data protection, audit rights, breach notification protocols, and exit strategies should be included to safeguard the organization’s interests.
5. Continuous Monitoring
Once a vendor is onboarded, continuous monitoring is crucial. Organizations should track the ongoing performance of vendors through regular audits, automated risk assessment tools, and security monitoring platforms such as Complyan. Continuous risk monitoring tools can help detect early signs of vulnerabilities, data breaches, or service outages.
6. Incident Response and Contingency Planning
Finally, organizations should have an incident response plan in place that addresses third-party risks. This plan should outline how to respond to security incidents, breaches, or service disruptions caused by third-party vendors. The incident response plan should also detail how to mitigate the impact on operations and communication strategies to inform stakeholders.
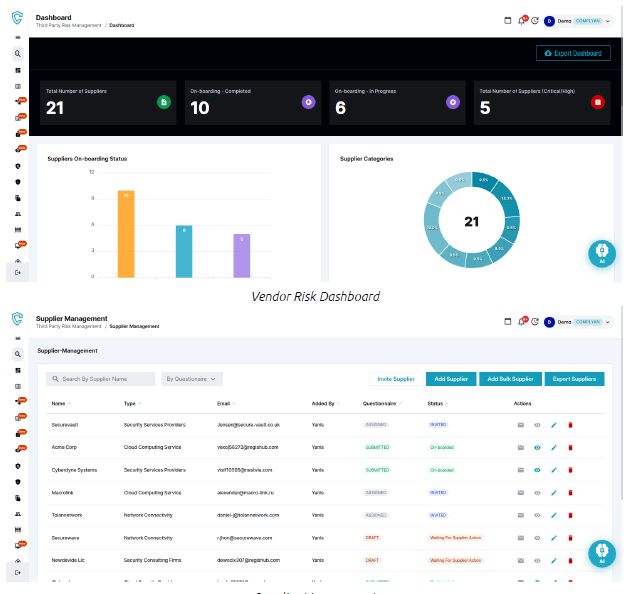
Vendor Risk Dashboards
A vendor risk dashboard provides a real-time view of third-party risk, helping you monitor, assess, and manage vendor security posture at a glance.
Conclusion
The risks posed by third-party vendors are concerns for businesses today. A comprehensive third-party risk management program enables organizations to proactively address cybersecurity, compliance, operational, and financial risks that could arise from vendor relationships. By thoroughly assessing third-party vendors and ensuring compliance with regulations, organizations can safeguard their critical assets and maintain business continuity. TPRM is no longer just a regulatory requirement’s an essential element of modern risk management and business resilience.
Are you ready to elevate your Third-Party Risk Management (TPRM) program? Discover how Complyan is revolutionizing third-party risk management





 Governance and Policy Management
Governance and Policy Management