The Digital Operational Resilience Act: Your Complete Implementation Guide

The European Union’s Digital Operational Resilience Act (DORA) represents a fundamental shift in how financial institutions approach cybersecurity and operational resilience. Coming into full effect on January 17, 2025, this regulation establishes uniform requirements across the EU financial sector, affecting over 20,000 entities including banks, insurance companies, investment firms, and their critical third-party service providers.
What Is DORA?
DORA is an EU regulation designed to strengthen the operational resilience of financial entities against ICT (Information and Communication Technology) risks. The regulation addresses a critical gap: while financial institutions have long been subject to prudential supervision, their digital infrastructure and cybersecurity practices lacked consistent oversight across member states.
The regulation creates a comprehensive framework that covers everything from risk management to incident reporting, ensuring that financial entities can withstand, respond to, and recover from ICT-related disruptions. Unlike previous fragmented approaches across different EU countries, DORA establishes harmonized rules that apply uniformly across all member states.
Who Must Comply?
DORA’s scope is extensive. The regulation applies to approximately 22,000 entities across the financial sector, including:
- Credit institutions and payment service providers
- Investment firms and crypto-asset service providers
- Insurance and reinsurance companies
- Pension funds and trading venues
- Central securities depositories and credit rating agencies
- Critical ICT third-party service providers (CTPPs)
The inclusion of third-party service providers marks a significant expansion of regulatory oversight. Cloud providers, data centers, and software vendors that serve the financial sector now face direct regulatory scrutiny if designated as critical.
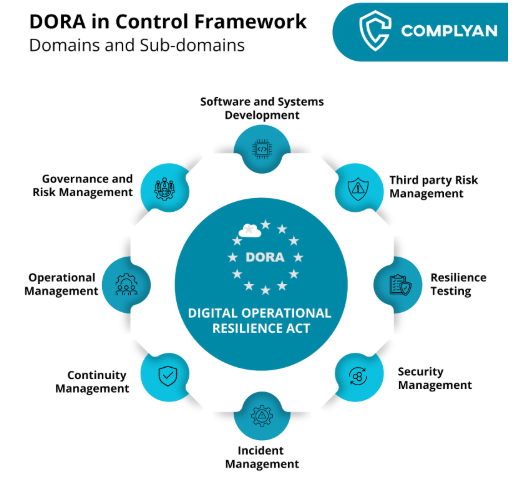
The Five Pillars of DORA

DORA’s framework rests on five interconnected pillars that create a comprehensive approach to operational resilience. Understanding these requirements is essential for any organization preparing for compliance.
DORA Framework Domains
1. ICT Risk Management
Article 6 of DORA requires financial entities to establish a robust ICT risk management framework proportionate to their size, complexity, and risk profile. This framework must be approved by the management body and include comprehensive policies covering:
- Risk identification and assessment methodologies
- Protection and prevention measures
- Detection mechanisms for anomalies and threats
- Response and recovery procedures
- Learning and evolving capabilities based on incidents
Organizations must maintain detailed inventories of all ICT assets, document dependencies between systems, and regularly review their risk management frameworks. The regulation emphasizes continuous monitoring and adaptation, requiring entities to update their risk assessments as their technology environment changes.
2. Incident Management and Reporting
DORA introduces standardized incident classification and reporting requirements across the EU financial sector. Financial entities must establish comprehensive incident management processes that include detection, logging, categorization, and escalation procedures.
The regulation distinguishes between different severity levels of incidents. Major ICT-related incidents must be reported to relevant authorities within strict timeframes: an initial notification within four hours of classification, followed by intermediate reports and a final report within one month. This structured approach ensures supervisory authorities maintain visibility into systemic risks across the financial sector.
Entities must also maintain detailed records of all ICT-related incidents, including minor ones that don’t require regulatory reporting. These records serve as valuable learning tools and demonstrate compliance during supervisory reviews.
3. Digital Operational Resilience Testing
Article 24 requires financial entities to implement a comprehensive testing program that validates their ICT systems and controls. The testing framework must be proportionate to the entity’s size and risk profile, encompassing various methodologies:
- Vulnerability assessments and scans
- Open source analysis and network security reviews
- Gap analyses and physical security assessments
- Source code reviews where applicable
- Penetration testing following TIBER-EU or equivalent frameworks
Significant entities must conduct advanced penetration testing at least every three years, simulating real-world attack scenarios. The regulation requires organizations to document testing results, remediate identified weaknesses promptly, and verify that remediation measures are effective.
4. ICT Third-Party Risk Management
DORA acknowledges that modern financial services depend heavily on external service providers, creating concentration risks and potential points of failure. The regulation establishes comprehensive requirements for managing these relationships.
Before entering any contractual arrangement with ICT service providers, financial entities must conduct thorough due diligence assessments. Contracts must include specific provisions addressing service levels, security requirements, audit rights, exit strategies, and data protection measures.
The regulation introduces the concept of Critical ICT Third-Party Service Providers (CTPPs) – vendors whose failure could pose systemic risk to the financial sector. These providers face direct oversight from EU authorities, including the European Supervisory Authorities (ESAs), marking an unprecedented extension of financial regulation into the technology sector.
Organizations must maintain comprehensive registers of their ICT service arrangements, continuously monitor provider performance, and develop strategies for managing concentration risk when multiple critical functions depend on single providers.
5. Information Sharing
DORA encourages financial entities to share information about cyber threats, vulnerabilities, and incidents. This collaborative approach aims to strengthen collective resilience across the sector.
Financial entities may participate in information-sharing arrangements to enhance awareness of ICT-related threats. The regulation protects entities engaging in these arrangements from potential liability, provided the information sharing occurs in good faith and complies with applicable laws including GDPR.
How Complyan Helps with DORA Compliance
Achieving and maintaining DORA compliance requires sophisticated tools that can manage the complexity of multiple control domains simultaneously. Complyan provides a unified platform specifically designed to address the comprehensive requirements financial entities face under DORA.
Integrated Risk Management: Complyan’s platform centralizes ICT risk management across all eight domains of the DORA framework. The solution provides automated asset discovery and inventory management, ensuring organizations maintain accurate records of their ICT infrastructure as required by Article 6. Real-time risk assessments and continuous monitoring capabilities enable financial entities to identify vulnerabilities before they become incidents.
Automated Incident Response: The platform streamlines incident management workflows, from initial detection through final reporting. Complyan automates the classification process based on DORA’s severity criteria and ensures notifications reach relevant authorities within required timeframes. Built-in templates and workflow automation reduce manual effort while maintaining compliance with strict reporting deadlines.
Third-Party Risk Oversight: Managing vendor relationships represents one of DORA’s most challenging requirements. Complyan’s vendor risk management module provides comprehensive due diligence frameworks, contract assessment tools, and ongoing monitoring capabilities. The platform maintains centralized registers of all ICT service arrangements, tracks critical dependencies, and alerts organizations to concentration risks.
Compliance Documentation: DORA requires extensive documentation to demonstrate compliance during supervisory reviews. Complyan automatically generates audit trails, maintains policy version control, and produces compliance reports that map directly to DORA’s requirements. This documentation capability significantly reduces the burden during regulatory examinations.
Testing Program Management: The platform includes features for planning, executing, and documenting resilience testing activities. Organizations can schedule assessments, track remediation efforts, and verify that corrective actions have been implemented effectively.
At Complyan, we help organizations build these frameworks by integrating ICT risk management into broader cybersecurity compliance strategies.
Preparing for DORA Compliance
With the compliance deadline now passed, organizations should focus on continuous improvement and demonstrating adherence to DORA’s requirements. Several strategic steps remain essential:
Conduct Comprehensive Gap Assessments: Organizations must evaluate their current ICT risk management frameworks against DORA’s requirements. This assessment should identify specific deficiencies in policies, procedures, technical controls, and governance structures.
Develop Remediation Roadmaps: Based on gap assessments, create detailed plans for addressing deficiencies. Prioritize remediations based on risk impact and regulatory criticality.
Review Third-Party Relationships: Audit all ICT service providers, assess their criticality, and ensure contracts include DORA-compliant provisions. This process may require renegotiating existing agreements to meet new standards.
Enhance Incident Response Capabilities: Establish or upgrade incident detection, classification, and reporting procedures to meet DORA’s strict timelines and requirements.
Implement Resilience Testing Programs: Design and execute comprehensive testing programs that validate your organization’s ability to withstand and recover from ICT disruptions.
The Broader Regulatory Context
DORA doesn’t exist in isolation. The regulation complements other EU frameworks including GDPR, NIS2, and the AI Act. Organizations must view their compliance efforts holistically, recognizing overlaps and synergies between different regulatory requirements.
The regulation also aligns with international standards like ISO 27001 and frameworks such as NIST. Organizations with existing cybersecurity programs can leverage these foundations while ensuring they address DORA’s specific requirements for the financial sector.
Organizations managing multiple compliance requirements can benefit from integrated approaches that address data privacy regulations alongside operational resilience mandates.
Enforcement and Penalties
DORA grants supervisory authorities significant enforcement powers. Non-compliance can result in administrative penalties up to 2% of an entity’s total annual worldwide turnover or €10 million, whichever is higher. For CTPPs, penalties can reach 1% of average daily worldwide turnover.
Beyond financial penalties, regulators can impose operational restrictions, require additional reporting, or mandate specific remediation measures. Repeated or severe violations could result in more drastic consequences affecting an organization’s ability to operate.
Conclusion
DORA represents a comprehensive approach to operational resilience in the financial sector. The regulation moves beyond traditional cybersecurity compliance, requiring organizations to build genuine resilience capabilities that enable them to withstand, respond to, and recover from ICT disruptions.
Success requires commitment from leadership, investment in people and technology, and a fundamental shift toward viewing operational resilience as a core business capability rather than a compliance checkbox. Organizations that embrace DORA’s principles will not only meet regulatory requirements but position themselves to operate more securely in an environment where digital resilience determines competitive advantage.





 Governance and Policy Management
Governance and Policy Management